Healthcare IoT Security: Exploring Risks and Finding Solutions
Updated: June 4, 2025
The Internet of Things (IoT) is an undoubted breakthrough in the conservative sphere of healthcare. From vital sign wearables to smart hospital beds, IoT guides us toward more responsive, precise, and effective patient care. But there’s a catch: Healthcare IoT Security.
Despite the strides, any device can potentially be an entry point for vulnerabilities. In a day and age where data privacy is king – especially in healthcare – how do we ensure these smart devices don’t become Trojan horses and compromise patient data?

We provide companies with senior tech talent and product development expertise to build world-class software. Let's talk about how we can help you.
Contact usThe answer is a comprehensive, future-proof approach to IoT security in healthcare. It’s about building robust systems against threats and fostering a culture of vigilance where everyone – from the device manufacturers to healthcare providers – knows the risks and their role in mitigating them.
Table of Contents
Understanding Healthcare IoT
Healthcare IoT, or healthcare Internet of Things or Internet of Medical Things, is a network of interconnected devices able to gather and share data without the intervention of humans. From wearable health monitors to high-tech hospital machinery, these gadgets leverage the internet, sensors, and software in collecting, interpreting, and communicating information on human health.
The idea behind Healthcare IoT is to facilitate improved patient outcomes and more effective overall operational efficiency in the healthcare scenario. Let’s explore this further:
- Patient Monitoring: Modern wearable gadgets such as heart rate monitors or glucose trackers allow the monitoring of patients on an ongoing basis. These devices transmit information to physicians in real-time, allowing them to detect abnormalities and quickly adjust treatment plans accordingly.
- Remote Care: IoT devices make it possible to provide telemedicine services to remote patients who do not like to visit medical facilities frequently. It means that the proper care of such patients can be ensured in time without having to carry out physical consultations, thus making it much easier and accessible for healthcare seekers.
- Asset Tracking: For hospitals and clinics, keeping tabs on the whereabouts and condition of medical equipment can be a real challenge. IoT-enabled asset tags help locate devices, ensuring they are maintained properly and available when needed.
- Data Collection and Analysis: IoT-connected medical devices can generate huge volumes of data. Such collected data may be used to describe trends in illness and patient reactions to various treatment modalities or environmental conditions.
- Operational Efficiency: Besides caring for patients, IoT can help operations by digitizing business processes. For example, sensors monitor environmental conditions within storage stores so vaccines or medicines may be stored at the right temperatures.
Healthcare IoT Benefits
The Internet of Things (IoT) in healthcare brings numerous benefits by changing the way providers offer medical services. Here is how connecting devices and systems capabilities help change the face of this industry:
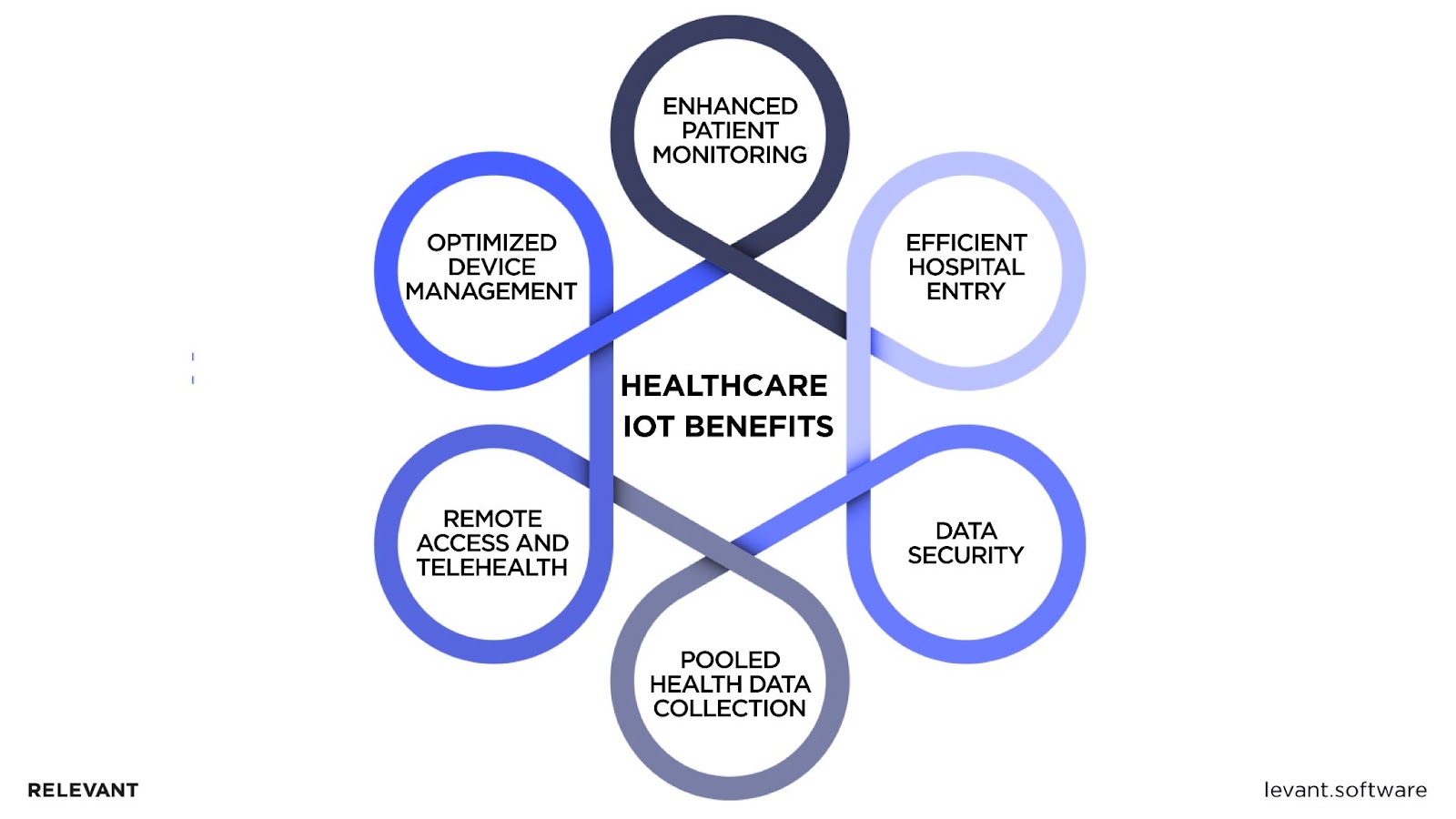
Enhanced Patient Monitoring
With connected medical devices, monitoring a patient’s vital statistics can be continuous and real-time. This means that abnormalities can be noticed early, and timely intervention can be made, reducing the likelihood of complications and saving lives.
Efficient Hospital Entry
The advanced features of IoT devices facilitate the patient journey regarding hospital entry. For example, medical information is stored on wearable devices, making it easy and quick to make an appointment or get a consultation without having to fill out forms again.
Data Security
With increasing reliance on electronic health records and healthcare databases, attention to IoT device security is imperative. Most advanced IoT systems have strong security to ensure patient data privacy and prevent false hacks.
Pooled Health Data Collection
Connected devices become the pivot in a large pool of patient data. This comprehensive data set, systematically stored in a healthcare database, provides a broader history of the individual to help healthcare professionals make informed decisions.
Remote Access and Telehealth
Most critical when physically going may be impossible, IoT facilitates remote consultation. Patients can relay their health data directly from connected devices to the doctors or healthcare professionals involved in providing care to maintain continuity.
Your Next Read: Telehealth: Benefits and Challenges
Optimized Device Management
With an increasing number of devices being used in hospitals and clinical institutions, managing the status and location of each instrument becomes vital. Management, maintenance, or even tracking in real-time of medical equipment is made efficient with IoT.
But along with the many benefits of IoT in healthcare, there are also security challenges of IoT in healthcare. It is important to analyze dangerous pitfalls that lie ahead as we progress even deeper into this digitally enhanced healthcare world.
Why Healthcare IoT is a Prime Target
In a digital age where information is currency, the healthcare sector, with its interconnected devices, poses a unique intersection of value and vulnerability. Let’s break down why the field is particularly susceptible:
- The Sensitivity of Medical Data: Health records don’t just reveal a person’s medical history. They often encompass personal information, from addresses and contacts to genetic data. This makes them highly desirable for a variety of reasons, be it identity theft, insurance fraud, or espionage.
- Lifelines in the Balance: Beyond data, the very operation of some IoMT devices can be life-sustaining. Think of devices that help regulate heartbeats or insulin levels. A compromise doesn’t just mean a breach of privacy but could interfere with the device’s core functionality, leading to direct physical harm.
- Rapid Integration, Varying Protections: As healthcare institutions rush to adopt the latest IoT technologies, the speed of integration can sometimes outpace the thoroughness of security measures. Additionally, ensuring consistent security can be a challenge for many device and software protocol manufacturers.
- The Connectivity Paradox: The inherent advantage of IoT — its interconnected nature — also becomes its Achilles’ heel. A weak link in one device can potentially compromise the entire network, increasing the risk many times over.
In the quest to implement technology to improve the quality of care, it’s vital not to lose sight of these security and privacy issues with IoT in healthcare. Recognizing why healthcare IoT is a prime target is the first step in bolstering its defenses and ensuring that innovation leads to better patient outcomes, not unintended risks.
Specific Healthcare IoT Security Threats
The fast-developing healthcare IoT security market indicates an increasing awareness regarding the numerous threats connected medical devices face. The massive adoption of technology indicates that security in the countless landscapes of IoT in healthcare is not only about avoiding data breaches but also aiding non-interrupted safe operations of medical devices. Let’s dive deeper into specific threats that underscore the security and privacy issues in IoMT development for healthcare.
Unauthorized Access
One of the most fundamental security issues in IoT healthcare revolves around unauthorized access. Many devices still come equipped with weak or even default passwords, offering low-hanging fruits for potential hackers. Additionally, the lack of two-factor authentication on a significant number of these devices increases vulnerabilities, presenting real IoT security healthcare concerns.
Malware and Ransomware Attacks
While advantageous, the interconnected nature of IoT devices can also be their downfall. These devices, if not properly secured, can serve as gateways for malware that can potentially spread contagiously throughout the network. Even more alarming, ransomware attacks are targeting this sector with alarming frequency, exploiting the sensitive nature of medical data to demand exorbitant ransoms.
Man-in-the-Middle (MitM) Attacks
The very essence of IoT rests on data transmission. MitM attacks prey on this, intercepting communications between two entities. The implications for healthcare are particularly severe, with eavesdropping or tampering leading to misdiagnosis or device malfunctions, highlighting the challenges in IoT healthcare security.
Distributed Denial of Service (DDoS) Attacks
DDoS attacks use compromised IoT devices to flood and crash systems. In a healthcare setting, where every second can be vital, such attacks can render crucial systems inoperable, leading to life-threatening disruptions.
In response to these threats, the healthcare IoT security industry is evolving, with healthcare IoT security solutions emerging that specifically address these challenges. However, it’s a constant race against time as hackers evolve and the medical healthcare IoT security landscape keeps shifting.
Consequences of Inadequate Healthcare IoT Security
It’s a growing market, and for good reason, as the healthcare industry becomes increasingly reliant on connected devices. However, even with all the best mitigation measures in place, threats are not mitigated, and the impact of a breach can extend well beyond the point of intrusion.
Ripple Effects of Medical IoT Data Breaches
A single lapse in healthcare IoT security can translate into massive data breaches, and there are manifold ripple effects:
- Financial Implications: Loss of data means heavy expenditures. From damage control to lawsuits, costs can reach sky-high levels, which can impact the financial health of healthcare facilities.
- Effect on Patient Trust: The bedrock of medical practice is patients’ trust in their doctors. A breach can destroy both, making patients unwilling to speak up to doctors or even come for treatment.
- Regulatory Outcomes: There are several areas with quite strict data protection laws. Non-compliance, especially due to breaches that might have been prevented, can lead to mammoth fines and more regulation, which amplifies the security and privacy issues of employing IoT in healthcare.
Potential Patient Harms
Aside from data, patients’ physical health is also at risk:
- Change in Device Function: Cyber-attacks have the potential to modify how medical devices operate, causing harm or fatality.
- Generation of False Data: Intentional manipulation may lead to the generation of false data that may mislead doctors and hence force them to make decisions on wrong treatments.
- Disruption of Critical Care: An attack could disrupt the life support systems of a patient or interrupt medication dispensers, creating life-threatening situations.
Given these impacts, manufacturers and healthcare providers alike are under pressure to engage healthcare software development partners who can not only address current threats but also prevent future vulnerabilities. This proactive approach is the bedrock upon which IoT’s safe and efficient integration in healthcare rests.
Best Practices for Healthcare IoT Security
There is, therefore, a need to have an all-inclusive security strategy for IoMT development services for healthcare that will protect the safety of both devices and the people they serve.
Device-Level Security
The integrity of connected medical devices should be guaranteed to act as the first line of defense against attacks:
- Regular Updates and Patching: It’s essential to update devices to guard against known vulnerabilities consistently. By promptly addressing and patching these security gaps, many attacks can be prevented.
- Strong Authentication Measures: Each IoT device should be equipped with robust authentication methods to deter unauthorized access.
- Role-Based Access Control: Not everyone requires access to all information. Access to specific data or device controls should be granted based on roles, thereby enhancing the security of the healthcare database and reducing potential breaches.
Network Security
A strong network is the foundation for any safe IoT environment:
- Data Transmission Encryption: Patient data in transit must be encrypted so that it will remain completely garbled even if intercepted.
- Segmented Networks for IoT Devices: Segregating medical IoT devices onto separate networks can contain the risk a single compromised device presents in its ability to compromise other devices potentially.
- Intrusion Detection Systems: It monitors the network continuously for any sign of unauthorized access or anomalous activities so it can prevent probable threats at an early stage.
Training and Awareness
Even the best security systems can be undone by human error:
- Regular Staff Training Programs: As IoT security healthcare protocols evolve, staff should be trained periodically to ensure they’re up-to-date with the latest best practices.
- Establishing a Culture of Security: Beyond formal training, cultivating an environment where security is everyone’s responsibility can go a long way.
- Patient Awareness and Engagement: Patients should be informed about the security measures in place and how they can contribute to safeguarding their data.

The Future of Healthcare IoT Security
The future for IoT device security appears bright, with several new technologies about to make significant impacts:
- AI in IoT Security: Artificial intelligence isn’t just a buzzword when it comes to IoT security. It can preemptively identify weak points and monitor threats as they arise. AI can alert databases holding confidential patient information to unusual behaviors, signaling potential breaches.
- Zero Trust Approach: The healthcare sector cannot take chances. In a zero-trust setup, every attempt to access a network from any device or user is scrutinized before approval. This minimizes risks, ensuring breaches don’t escalate.
- Blockchain for Data: Accuracy in patient data is essential. With its decentralized, tamper-resistant nature, blockchain ensures that once data is recorded, it remains consistent and genuine, basic when sharing information across various health platforms.
It’s clear that as healthcare increasingly integrates tech, security must keep pace. Protecting data is vital, but equally important is ensuring that this integration maintains patient trust and safety.
Healthcare IoT Security: Conclusion
Healthcare swiftly adopts IoT, opening doors to enhanced patient care and streamlined data processes. Yet, this progress comes with its set of concerns. Addressing these risks isn’t straightforward, but collaborating with knowledgeable IoT software development partners like Relevant can ease the burden. By seeking our specialized assistance, you can better protect your patient data and fortify your networks against threats.
Do you need a trusted partner for cybersecurity services for healthcare or other domains? We’re here to help.
Our core services:
Do you want a price estimate for your project?
Do you know that we helped 200+ companies build web/mobile apps and scale dev teams?
Let's talk about your engineering needs.
Write to us