An Ultimate Guide to The Essentials of Cloud Security in Healthcare
Updated: June 4, 2025
Cloud security in healthcare is more than a technical issue—it’s a matter of public trust and safety. According to Cloud Security Report 2023, around 76% of organizations are deeply worried about their cloud security. About 59% of executives view misconfigurations as a major risk, and if you’re one of them, you’re in good company but also in urgent need of guidance. The consequences of inadequate cloud security are far-reaching. From unauthorized access to sensitive patient records to the disruption of critical medical services, the risks are real and immediate.
This article is your comprehensive guide for understanding and implementing robust healthcare cloud security measures. We’ll provide clear, actionable steps to improve your cloud security, helping you protect both patient data and your organization’s reputation.

We provide companies with senior tech talent and product development expertise to build world-class software. Let's talk about how we can help you.
Contact usTable of Contents
The Rising Importance of Cloud Security in Healthcare
The cloud offers numerous advantages—flexibility, cost-efficiency, and scalability, among others. However, they come with some challenges, particularly regarding security issues with cloud computing in healthcare.
Recent data paints a compelling picture: 39% of organizations run over half of their workloads in the cloud. But this rapid cloud adoption has outpaced our ability to secure it. A concerning 58% of organizations admit having a skills gap in deploying cloud security, and 52% are grappling with data protection in multi-cloud environments. Moreover, 24% have faced a security incident related to public cloud use, with issues like misconfigurations, account breaches, and exploited vulnerabilities leading the list.
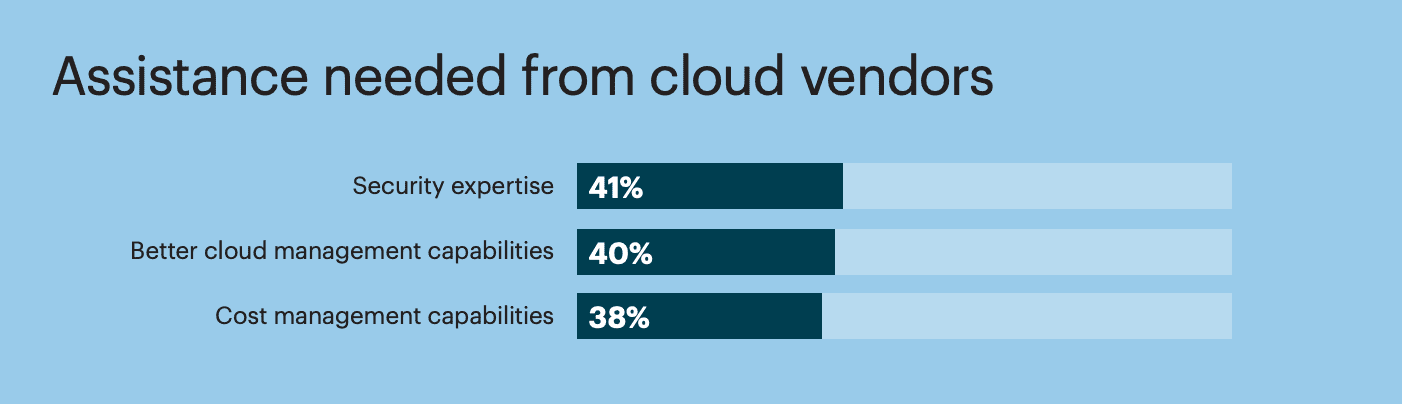
Source: Hubspotusercontent
The risks of cloud computing in healthcare are real and present dangers that can compromise patient data and disrupt essential medical services. The stakes are incredibly high. A single breach can erode patient trust, result in hefty fines, and even put lives at risk.
Understanding the cloud security threats for healthcare will help you mitigate them effectively. And further, we’ll explain how to fortify your security posture and protect your data in cloud environments.
What is Cloud Security?
Cloud security is the robust set of policies, technologies, and controls deployed to protect data, applications, and infrastructure in the cloud. But let’s break it down further, especially focusing on cloud computing security in healthcare, a field where the term takes on life-or-death significance.
Think of cloud security as the vault that keeps your healthcare data safe. But unlike a traditional vault, this one is accessible from anywhere by those who have the right keys—be it doctors, nurses, or administrators. The challenge? Make sure those keys don’t fall into the wrong hands while ensuring the right people can access the data they need to provide critical care.
In short, protecting your healthcare cloud computing means creating an environment where data can flow freely yet securely. To do that, you should focus on three key areas:
- Data confidentiality to ensure only authorized staff can access the data;
- Data integrity to make sure the data stays unchanged and reliable;
- Data availability to make data easily accessible when and where it’s needed.
Types of cloud service models
Let’s review the basic types of cloud services for healthcare to understand the advantages and challenges of each. It would be particularly helpful for organizations that are only planning to migrate to the cloud but are unsure which model will fit them best.
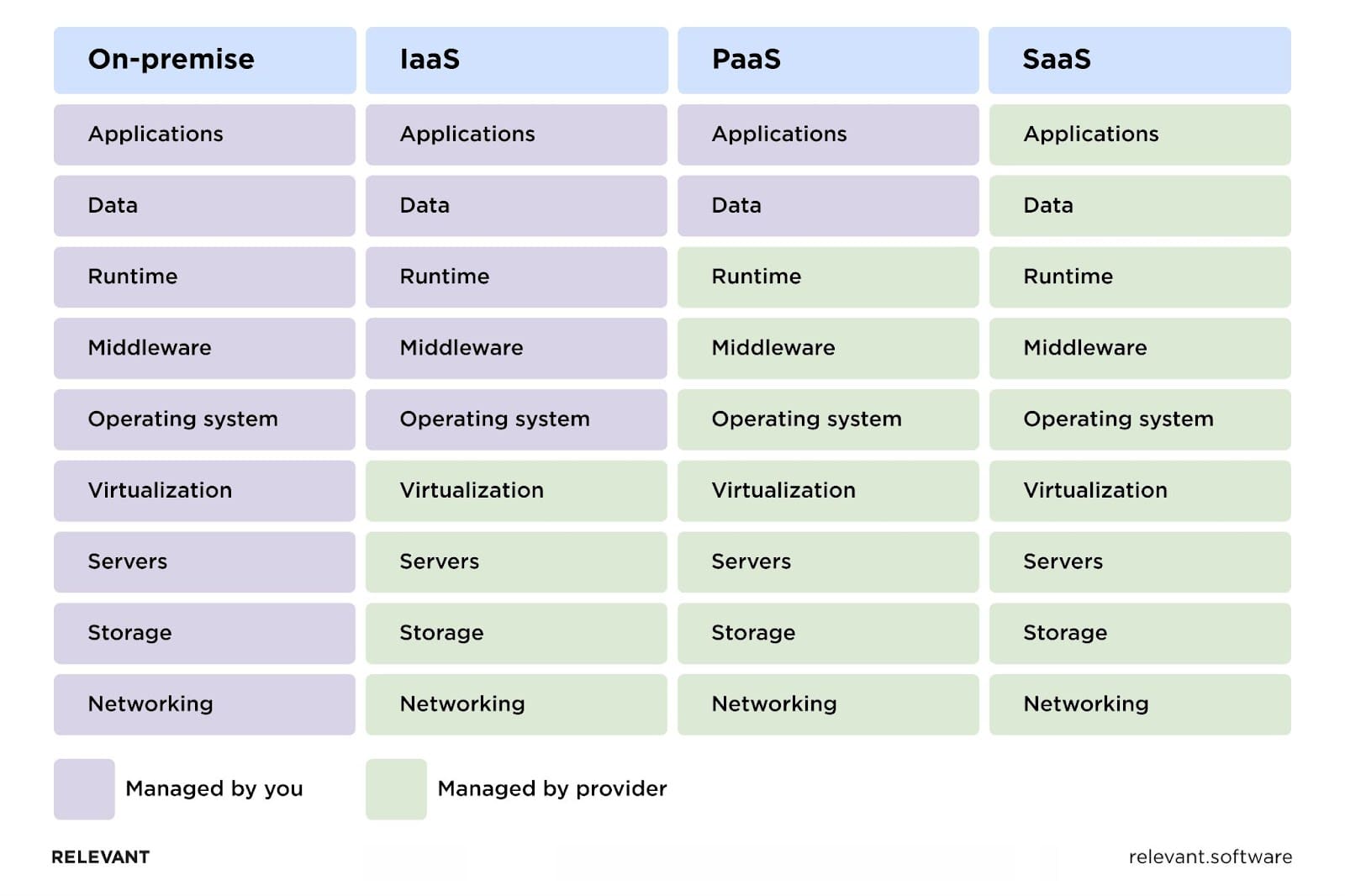
SaaS: Software as a Service
SaaS is a ready-to-use service where everything is prepared for you, and all you have to do is start using it. SaaS solutions for healthcare might include electronic health records (EHRs), telemedicine platforms, or patient management systems. You access the software through a web browser, and all the technical details—maintenance, security, updates—are handled by the vendor. It’s convenient, but it also means you have less control over the data and its security. That’s why choosing healthcare cloud solutions that comply with industry regulations and offer robust security features is crucial.
IaaS: Infrastructure as a Service
If SaaS is a plug-and-play solution, then IaaS is like an operating room that’s fully equipped but doesn’t run itself. You get the essential equipment—servers, storage, networking—but you’ll need to configure and manage them yourself. With this model, you’ll have more control over your cloud services for healthcare and can customize them to fit your specific needs. However, with great control comes great responsibility. You’ll have to manage and secure the infrastructure, which can be a complex task.
PaaS: Platform as a Service
PaaS sits somewhere in between. PaaS gives you a platform that includes things like operating systems, databases, and development tools. It’s particularly useful for developing custom healthcare applications quickly because you don’t need to worry about the infrastructure. Yet, like IaaS, your staff should be skilled enough to manage it effectively. So, you might require professional healthcare cloud solutions development to build secure and reliable solutions.
If you have any questions left on cloud models or how to migrate to the cloud, you can always rely on cloud migration services provided by Relevant to find the answers to your questions.
Why Cloud Security is Crucial in Healthcare
During this year alone, the Office for Civil Rights reported 434 cyber attacks on the medical sector, with a staggering 303 of these targeting network servers. The most common type of breach? Hacking and IT incidents accounted for 348 cases, followed by unauthorized access or disclosure in 75 instances. These numbers are striking and reveal a real picture of weak system security.
So, why is security in healthcare so crucial? Because the information that flows through medical facilities is a goldmine for cybercriminals. It includes personal medical histories, social security numbers, and other valuable data. Hackers can exploit this information for identity theft or sell in the Internet’s darker corners.
Now, let’s consider the stakes. According to a recent report, the consequences of cyber-attacks are severe: 43% resulted in data breaches or theft, 22% disrupted healthcare services, and another 26% affected services not directly related to healthcare. So, a single security breach can expose thousands of patient records, putting individuals at risk of identity theft, fraud, and other forms of exploitation. Healthcare providers could face legal repercussions, hefty fines, and a loss of public trust that can take years to rebuild. In a worst-case scenario, compromised data could impact patient care, leading to incorrect diagnoses, longer patient stays, or even increased mortality rates.
The move to cloud-based healthcare is driven by the need for efficiency, accessibility, and cost-effectiveness. However, this transition also opens the door to new types of vulnerabilities. The bright side is that these risks are manageable. With the proper healthcare cloud security measures in place, the cloud can be as secure—if not more so—than traditional on-premises solutions.
Modern Trends in Healthcare Cloud Security
Staying updated on current trends is more than just a best practice—it’s a survival necessity. As cyber threats grow more complex, the key to robust cloud security in healthcare lies in staying one step ahead.
Increased Adoption of Hybrid Cloud Environments
In fact, hybrid cloud use has surged from 25% to 42.5%, signaling a growing confidence in this approach. Why is that? Because hybrid cloud services offer a perfect blend: the strong security of private clouds and the scalability of public ones. So, it offers flexible yet secure cloud storage in healthcare for managing the ever-increasing volumes of sensitive patient data.
Healthcare providers can store critical, sensitive information in a private cloud, where they have more control over security protocols. At the same time, they can leverage the vast resources of a public cloud for less sensitive yet resource-intensive tasks like data analytics or administrative functions. Thus, by opting for this approach, your medical organization can tailor your cloud environment to meet specific needs and compliance requirements.
AI and Machine Learning in Cloud Security
In recent years, we’ve observed many organizations increasingly adopt AI and ML technologies to navigate an ever-changing landscape of cyber threats. To be precise, 64% of executives have already integrated AI into their security frameworks, while another 29% are actively considering its implementation. So, how these advanced technologies can shield your healthcare cloud solutions against increasingly sophisticated cyber-attacks?
AI and machine learning in healthcare can look through mountains of data in real time, identifying unusual patterns or potential threats that would take a human team hours, if not days, to spot. It allows healthcare providers to react to security incidents faster and even prevent them before they occur.
Imagine a scenario where a healthcare worker accidentally clicks on a phishing email, putting the entire network at risk. ML algorithms can detect this unusual activity almost instantly and flag it for immediate action or even block access automatically. This rapid response is the difference between a minor hiccup and a full-blown data breach.
Beyond threat detection, AI and ML can also help healthcare organizations comply with regulations, manage access controls, and even predict future security trends based on current data.
Emergence of Zero Trust Security Models
Gone are the days when security measures focused solely on building a solid perimeter to keep threats at bay. The zero trust model acknowledges that security risks can originate from anywhere, including inside your organization. It’s like having a state-of-the-art security system not just at the entrance of a hospital but at every door, window, and even the medicine cabinet. Every user, device, and network flow is treated as a potential risk and must be verified before gaining access to sensitive data.
Simply put, zero trust models operate on a simple but effective principle: verify every access request, irrespective of its origin. It shifts the focus from merely preventing unauthorized access to continuously monitoring and validating the security posture of everything that interacts with your healthcare cloud environment. That’s why this approach has rapidly become a cornerstone in cloud security developments in healthcare.
Common Cloud Security Challenges in Healthcare
As medical organizations increasingly rely on cloud computing, they can face a host of security issues with cloud computing in healthcare they need to address to protect sensitive patient data. Understanding these challenges is the first step in building a strong security strategy for your organization.
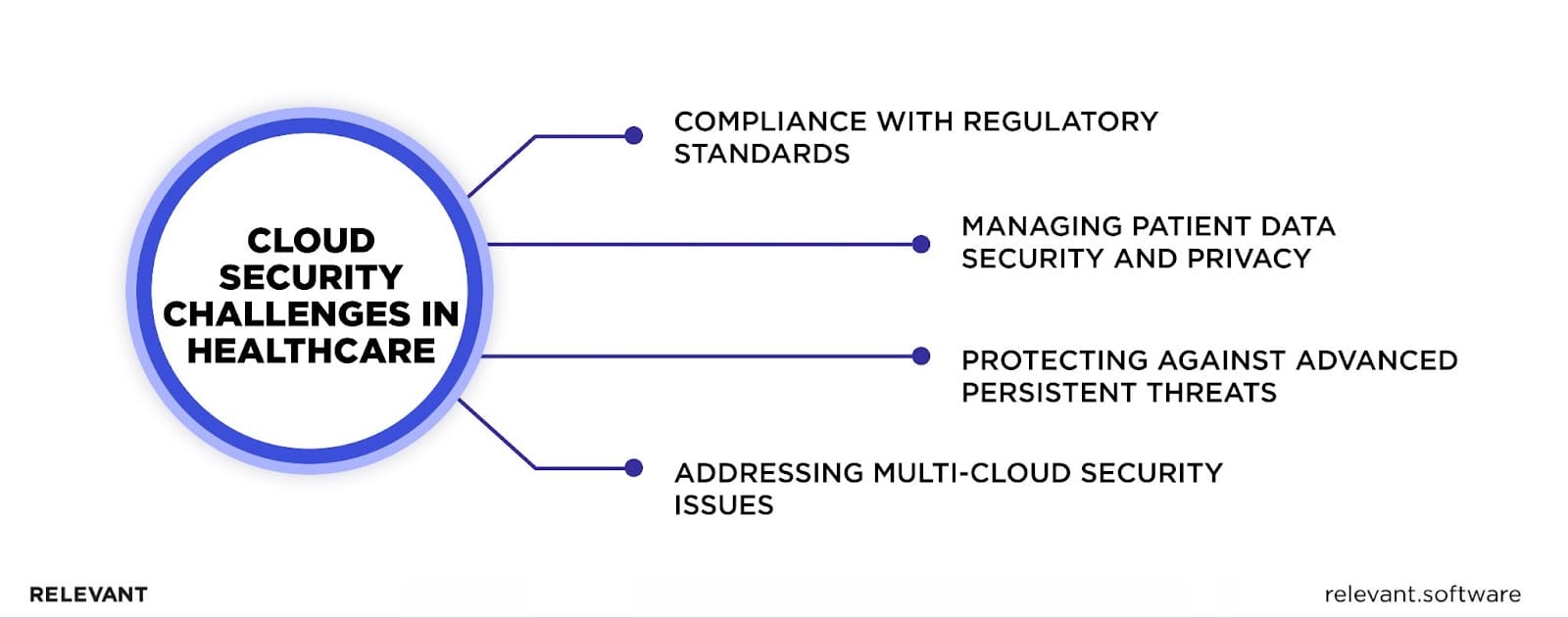
Compliance with Regulatory Standards (HIPAA, GDPR)
Compliance with regulatory standards like HIPAA in the United States or GDPR in Europe isn’t optional; it’s a legal requirement, and the penalties for violations can be severe. These regulations aim to protect patient data, but they also add some complexities to cloud security protocols.
Healthcare organizations must ensure that their cloud services providers are compliant, which often involves rigorous audits and continuous monitoring. Rather than ticking off a checklist, the goal is to integrate these standards deeply into your cloud security strategy. It includes encrypting patient data, controlling who has access to it, and ensuring it can be easily but securely shared among healthcare providers when necessary.
Managing Patient Data Security and Privacy
With healthcare data being a prime target for cybercriminals, the need for robust patient data management in the context of cloud computing security in healthcare has never been more urgent. The data isn’t static; it’s continually moving, accessed, and updated by various stakeholders, from healthcare providers to insurance companies. Each interaction point poses a potential security risk, complicating the task of securing cloud services for healthcare.
Adding to this complexity is the need for compliance with regulatory standards. The cloud is part of a broader ecosystem that includes third-party vendors and cloud service providers. Ensuring that each component in this interconnected system meets industry regulations augments the challenge of maintaining a secure and private healthcare cloud environment.
Protecting Against Advanced Persistent Threats (APTs)
Unlike typical cyberattacks that aim for quick hits, APTs are long-term infiltrations designed to steal data over an extended period. They’re the cyber equivalent of a slow leak that can go unnoticed until significant damage is done. And this makes them particularly dangerous.
Improving cloud security in healthcare requires a multi-faceted approach to defend against APTs. Real-time monitoring is crucial, but it’s not enough. Healthcare organizations also need predictive analytics that can identify abnormal patterns of behavior before they grow into full-blown breaches. It’s one of the latest cloud security developments in healthcare that combines machine learning algorithms with traditional security measures to create a more resilient defense system.
Addressing Multi-Cloud Security Issues
The rise of multi-cloud environments has brought flexibility and complexity to healthcare cloud security. While using multiple cloud services lets you optimize performance and reduce costs, it also creates a fragmented security landscape. Each service in the cloud has its own security protocols, and ensuring consistent protection across all platforms becomes more complex.
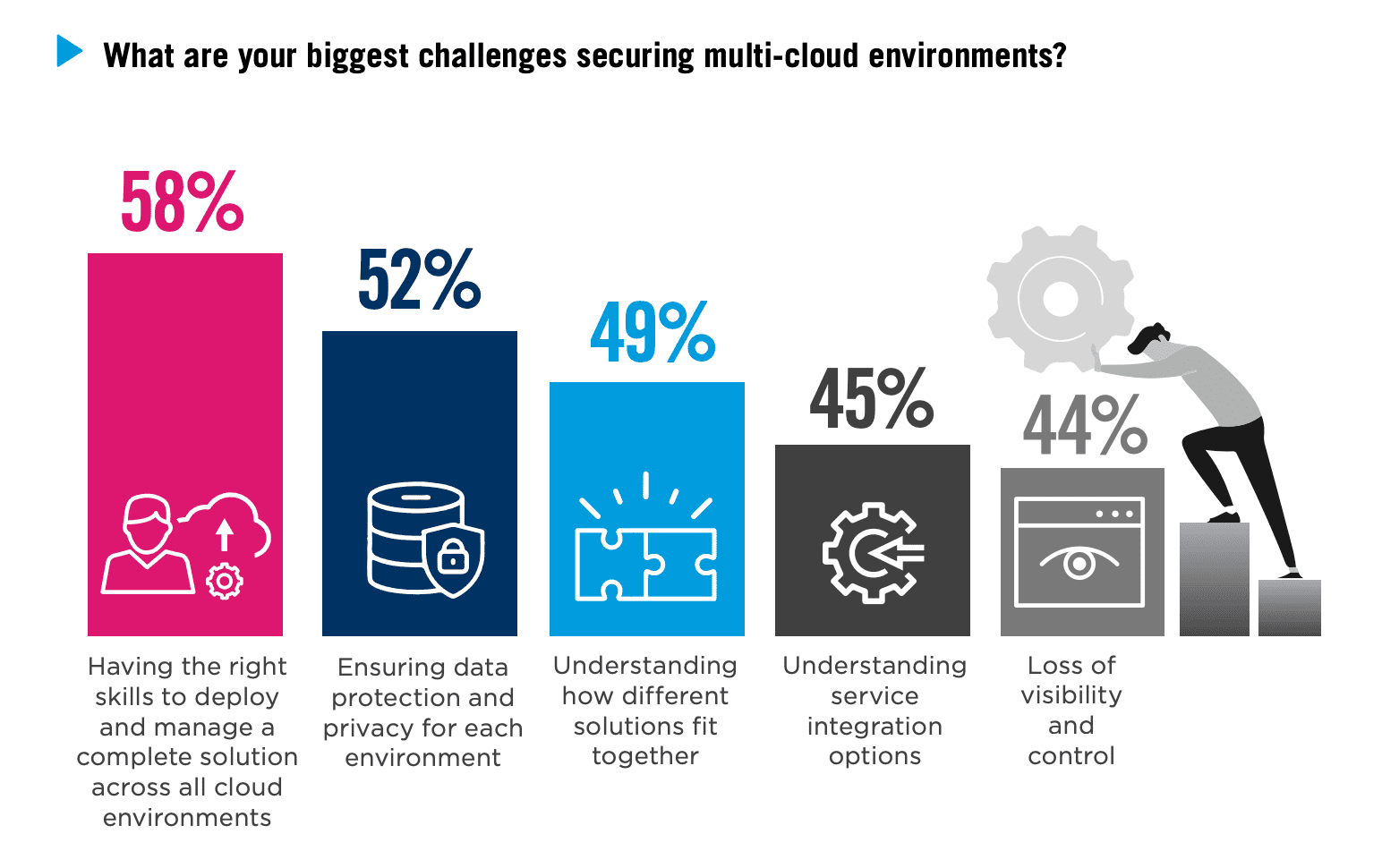
Source: Checkpoint
Many healthcare organizations often find themselves handling different security measures for each cloud service they use. However, this fragmentation can lead to gaps in security, making the system vulnerable to cyberattacks. The main challenge here is to develop a cohesive security plan that will work smoothly with all cloud services your organization uses.
Implementing Effective Cloud Security Measures in Healthcare
With sensitive patient data and critical medical services at stake, there’s no room for error. That’s why we highlight the practical tips and strategies that helped our clients strengthen their cloud computing healthcare security.

Developing a Comprehensive Cloud Security Strategy
Creating a well-thought-out security strategy is vital in any case and for every business. Risk assessment should be the first thing to do to identify vulnerabilities specific to your organization. Besides the technical aspect, consider human errors because they also can lead to security breaches. Once you get a clear understanding of the risks, you can prioritize them and develop targeted solutions.
Regulatory compliance is another cornerstone of an effective strategy. Guidelines from HIPAA, GDPR, or other relevant regulations for data storage and transmission must be integrated into your cloud security in healthcare.
Finally, your strategy should be dynamic and capable of adapting to new threats and evolving technologies. Regular updates to security protocols, frequent audits, and continuous monitoring are essential to staying ahead of potential risks.
Employing Encryption and Data Loss Prevention Techniques
Encryption should be a standard in healthcare cloud security. It converts plain text data into a coded form using an algorithm and an encryption key. Data can only be decrypted to its original form by those possessing the right decryption. So, even if a cybercriminal gains access to the data, it remains unreadable and, therefore, useless. Data can only be decrypted by those possessing the right key, and Data Loss Prevention (DLP) methods offer an extra safeguard.
Data loss prevention (DLP) techniques offer an extra layer of security. These tools help you monitor and control data transfer, ensuring sensitive information doesn’t leave the secure network without proper authorization. In the context of cloud and healthcare, DLP can prevent accidental leaks by employees, block unauthorized access, and even halt data transfers to compromised devices.
Embracing Multi-factor Authentication (MFA)
Multi-factor Authentication (MFA) is a good practice in healthcare cloud computing, and it’s easy to see why. Traditional login credentials can’t protect against increasingly sophisticated cyberattacks anymore. MFA helps with that and enhances protection by requiring multiple verification methods. Apart from a password, it will require confirmation from your mobile device or fingerprint or facial scan to provide access to your system.
So, MFA ensures that the likelihood of unauthorized access is minimal, even if your password is compromised. For example, after entering a password, you might receive a text with a verification code or need to confirm your identity through biometric data like a fingerprint. It’s something cybercriminals can’t bypass to get access to your system or data.
Leveraging Identity and Access Management (IAM)
At its core, IAM controls who can access what is within your cloud-based healthcare system. It’s like a digital ID card that not only proves you are who you say you are but also outlines what you’re allowed to do once you’re in the system.
On top of that, IAM lets healthcare organizations set up access controls based on job roles, restricting employees to only the data they need for their specific tasks. For instance, a doctor might have access to patient medical records but not financial data. Such an approach effectively mitigates cloud security threats for healthcare organizations and minimizes the risk of internal threats, whether accidental or malicious.
Ensuring Regular Audits and Security Assessments
Routine check-ups of your cloud environment will offer a detailed snapshot of your current security posture, highlighting vulnerabilities you might not even know. It could be outdated software, poor access management, or gaps in data encryption. The scrupulous audits of your cloud infrastructure, data flow, access controls, and the security culture within your organization will help you identify weak spots before they can be exploited.
Incorporating regular audits into your healthcare cloud security strategy offers a twofold benefit. First, it keeps your organization in line with regulatory requirements and provides actionable insights to improve your security measures continually.
Fostering a Security-Oriented Culture
Promoting a culture where security is primary is often overlooked, but it’s essential for building effective healthcare cloud security. While technology is vital, the human element cannot be ignored either. Even the most robust security solutions can be compromised by simple human error or negligence.
So, what does a security-first culture look like? All your employees—from healthcare specialists and nurses to administrative personnel—actively participate in the organization’s security efforts. They should undergo regular training on best practices, such as how to identify phishing emails or the importance of strong, unique passwords. You should also foster a culture where staff can report suspicious activities without fear.
Cloud Security in Healthcare: Key Takeaways
Ensuring solid cloud security in healthcare is no small feat, yet the advantages of a well-protected cloud infrastructure are worth it. Think about streamlined operations, enhanced patient care, and a reputation as a reliable healthcare provider – all this is achievable with digital transformation. And collaboration with industry experts can help you accelerate this transition.
Relevant Software, a leader in healthcare IT consulting services, offers tailored healthcare cloud solutions designed to meet your specific needs. We can assist you in securely migrating, optimizing, and managing cloud workloads. Our deep expertise in handling different cloud models helps us deliver efficient, reliable, well-governed cloud systems that bring real value to our clients.
Also, read more about the impact of nanobots in the healthcare industry.
FAQ
Our core services:
Do you want a price estimate for your project?
Do you know that we helped 200+ companies build web/mobile apps and scale dev teams?
Let's talk about your engineering needs.
Write to us