How to Build a Resilient Digital Infrastructure in the Banking Industry
Updated: September 16, 2024
The 2020s brought next-generation technology transformation to financial services, and digital resilience has become one of its imperatives. With the economic situation characterized by profound uncertainty, building resilient digital infrastructure is a precautionary measure that can ensure business continuity in normal and adverse cases.
At Relevant, we know how important business resilience is. Your banking system may have a robust protection system in place, yet stats show that 70% of breaches are caused by external factors. Having security-first thinking and a team of experienced engineers, we provide cybersecurity services and help businesses withstand cyberattacks with no or minimal harmful outcomes.

We provide companies with senior tech talent and product development expertise to build world-class software. Let's talk about how we can help you.
Contact usThis article serves as a roadmap on how to become a digitally resilient business and ramp up your company’s tech productivity. Let’s dive in.
Table of Contents
Why should digital infrastructure be resilient?
In August 2020, the New Zealand Stock Exchange’s network provider had an extended DDoS attack that lasted several days and resulted in shutting down all their operations. The same month, the Government of Canada reported that its GCKey, a critical single sign-on system, and CRA accounts had been subject to credential stuffing attacks aimed at stealing COVID-19 relief funds.
Meanwhile, in October, the European Central Bank’s primary payment system was down for almost 11 hours. A software defect that caused the disruption affected the bank’s Target2 critical function. These are only a few examples of how persistent cyber threats can put down entire systems.
Financial organizations have always been the prime target of cyberattacks. But, today, the risks are even higher. The banking industry is proliferating and growing at a rate of knots. High payoffs, the relatively low risk of detection together with possible flaws in the security systems work as an invitation for scammers.
Despite significant policymaking, the number of attacks against major financial institutions has grown. According to the Boston Consulting Group, financial services firms are 300 times more likely than other companies to become victims of a cyberattack. They not only exploit vulnerabilities but also result in business process disruption, sensitive and financial data loss. Besides, dealing with those attacks and their aftermath carries a higher cost for banks and financial service businesses than for any other sector.
With cyberattacks being almost inevitable, the only way to protect your financial system, data, and customers is to take proactive measures—implement digital business resilience.
With cyberattacks being almost inevitable, the only way to protect your financial system, data, and customers is to take proactive measures—implement digital business resilience. It’s a must to be ready for any stressful scenarios and, in case they happen, have a proper action plan to stay afloat with minimal losses.
Why cyber resilience is important to fintech companies
Fact: 98 of 100 leading and well-funded fintech startups are vulnerable to cyberattacks and have security, privacy, and compliance issues. All these factors make them a juicy contract for scammers. While traditional protective measures can only hold them up for some time, they cannot wholly dismiss them.
But it’s not only fintech startups that are exposed to the increased risk of cyberattacks. Banks are facing the same challenges. The COVID-19 pandemic accelerated the digitalization of the banking industry. Yet, the downside of moving most services online is the boost in cybercrime: the number of attacks against the financial sector increased 238% globally from the beginning of February to the end of April 2020.
Most often, scammers choose the weakest link in the chain, which is end-users. That’s why many companies believe that security cost increases have become completely unsustainable in the constant struggle of staying ahead of hackers. But there is another, more financially viable way to protect your company—building cyber resilience.
Fintech cybersecurity is focused on preventing hackers from attacking and compromising your system and data. It’s one of the core elements of any financial system and should be approached by a responsible in-house team. And in case they lack the required competencies, it can be done by outsourcing cybersecurity to external vendors.
Cyber resilience, in turn, is about detecting, identifying, and responding to attacks or technology failures and recovering after them with the slightest customer harm, reputational damage, and financial losses. It is now being considered as the future of data protection.
Main areas of cyber resilience in the banking industry
An effective cyber resilience strategy encompasses cybersecurity as the first step but goes far beyond it, focusing on managing the three largest types of risks:
- Risks related to IT systems and infrastructure. Fintech technology systems and infrastructure often serve as a starting point for cyberattacks. Knowing what technology risks may occur and implementing proper vulnerability management are important aspects of building a cyber-resilient business.
- Operational risks. Customer communication failures, inability to generate transactions or problems with billing are operational risks any financial firm can face. They can also impact your bank reputation and lead to potential losses.
- Risks connected to fraud and financial crime. Scammers often search for gaps and vulnerabilities in banking security systems such as payment systems, digital banking services, and electronic trading. That’s why investing in risk mitigation measures is vital to be able to protect company assets.
Once implemented, cyber resilience allows banks and financial services businesses to spin up a quick analysis of any kind of these risks and immediately respond to it for the best possible business recovery.
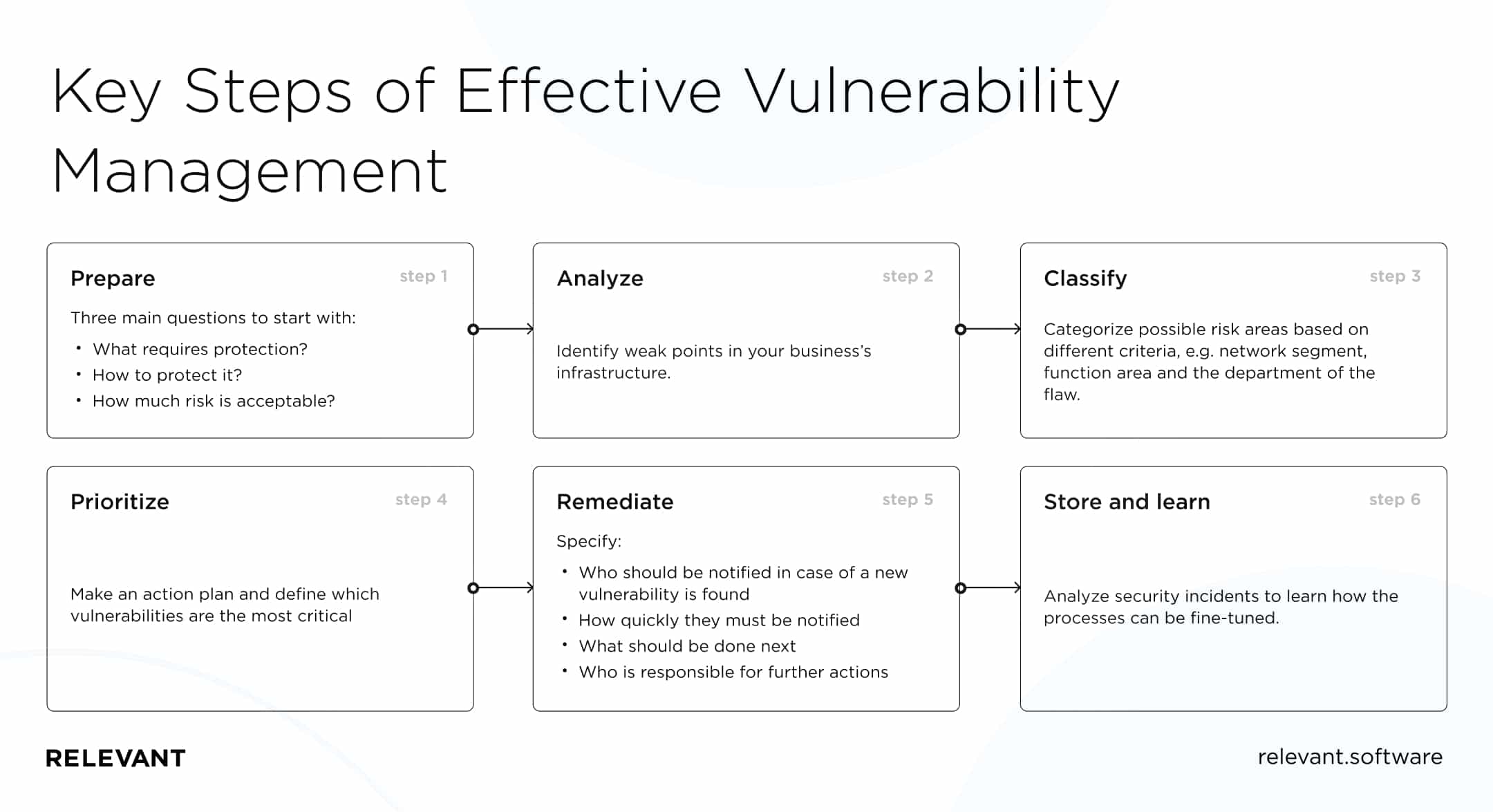
Key steps of effective vulnerability management
Vulnerability management is an essential element of a sustainable digital resilience framework. Its primary mission is to identify and eradicate vulnerabilities that hackers and scammers may use to compromise your system. Vulnerability management, if handled right, can help your financial services business be one step ahead of scammers.

We provide companies with senior tech talent and product development expertise to build world-class software. Let's talk about how we can help you.
Contact usEffective vulnerability management consists of six major steps. Let’s take a closer look at each one and explain their primary objectives.
Step 1. Prepare
You need to answer three main questions to start with:
- What requires protection?
- How to protect it?
- How much risk is acceptable?
Having the answers to these questions will help your IT team decide how to build digital resilience and ensure regulatory compliance.
Step 2. Analyze
You need to perform a safety and digital resilience assessment and analyze the outcomes. Vulnerability scans will help you identify weak points in your business’s infrastructure. The discrepancies with configuration specifications or outdated parts of your system can make your system vulnerable to hacks and cyberattacks.
Step 3. Classify
Once you assess the possible risk areas, you need to categorize and classify them based on different criteria. These could be the network segment where the flaw is located, the function area, the department it belongs to, or any other criteria defined by your company.
Step 4. Prioritize
It’s crucial to make an action plan and define which vulnerabilities are the most critical and should be handled with the highest priority.
Step 5. Remediate
Remediation is a process of eliminating all the vulnerabilities found during the previous steps. In this step, you specify:
- Who should be notified in case of a new vulnerability is found
- How quickly they must be notified
- What should be done next
- Who is responsible for further actions
Step 6. Store and learn
The last step is about storing key data about the vulnerability, including the time it was first detected and how long it took the team to rectify it. Analyzing security incidents is helpful in further audits to learn how the processes can be fine-tuned.
Vulnerability management is a dynamic and continuous process. You can do it internally or hire a cybersecurity expert to help you approach this task in the most effective way. Once you establish it, vulnerability management would help your company know its “enemies” and strengthen its abilities to resist attacks. And, if they happen, continue to function.
Case example
Building a digitally resilient IT infrastructure is not a cakewalk, but it is essential for fintech companies to keep up with the time and their competitors. One of the prominent digital resilience examples is the transformation of a large Asian bank.
The bank had legacy IT infrastructure with old databases, dispersed teams, and, if that’s not enough, manual ticket-based workflows. The described state of things made it vulnerable to cyberattacks and data loss. Besides, it was almost impossible to modernize its infrastructure. But to stand the competition and quickly develop and test new products, it was essential to adopt new resilient technology and move to the cloud.
They began with setting clear objectives and result targets to:
- Reduce manual, repetitive work
- Improve security processes
- Automate testing processes
To achieve these goals, they started with restructuring teams, making their work more collaborative and integrated. The bank’s leadership also rebalanced the ratio of engineering and operations talent on board and gained the support of advanced engineers to adopt the site reliability engineering (SRE) model. This allowed them to create a scalable, highly reliable, and resilient digital platform.
As a result, its new operating model helped the Asian bank speed up the deployment time from weeks to hours, increase digital resilience, and reduce operating costs by 30% (50% compared with revenue).
Develop your cyber resilience plan
Digital transformation and business resilience go hand in hand, helping financial organizations grow stronger in the face of uncertainty. Investing in digital resilience on top of traditional protective measures can help financial service businesses create a sustainable competitive advantage and get ready for attacks.
Relevant’s experts can help you build a digital transformation roadmap and develop your cyber resilience plan, taking into account all the peculiarities of your business. Contact our team today to build a resilient digital infrastructure for your financial services business and stay ahead of the ever-evolving threats.
Our core services:
Do you want a price estimate for your project?
Do you know that we helped 200+ companies build web/mobile apps and scale dev teams?
Let's talk about your engineering needs.
Write to us