Dependency Check Guide to Help You Find Vulnerabilities in Open-source Software Components
Frameworks, libraries, and other software components massively run with full privileges. Therefore, an exploited cybersecurity vulnerability in such a module can result in a security breach, loss of data, or even control over your servers. Using software components with known vulnerabilities can compromise your cybersecurity defenses and lead to various attack scenarios.
But can there be so many vulnerabilities? Some estimates show that up to 44% of apps use open-source components with known vulnerabilities! In addition, up to 50% of Global 500 companies have vulnerable open-source components in their apps. It shouldn’t come as a surprise when you hear about the next brand, big or small, falling victim to a cybersecurity breach.
from 25 countries outsourced software development to Relevant
We provide companies with senior tech talent and product development expertise to build world-class software.
What’s even scarier, the open-source ecosystem is much more fragile than we prefer to think — and definitely not more secure than proprietary software. You might have heard how one developer nearly destroyed the Internet by deleting 11 lines of code… Rude awakenings like that are a nightmare of any business that uses third-party software modules. How to make sure the next crash doesn’t happen to your company? Regularly perform in-depth dependency checks to find and remove vulnerabilities in open-source components you use.
Relevant Software is a software development company that has excellent cybersecurity expertise. We mostly build SaaS web applications, including fintech solutions, and securing them is our everyday job. The dependency check guide below is based on our experience, so keep on reading to discover the best methods of finding and removing vulnerabilities in open-source software components.
Read also how to hire a cybersecurity expert as well as Site Reliability engineer.
Method 1: Use a tool
Due to a massive demand for examining cybersecurity dependencies, you can use multiple products and open-source tools to check your app code for vulnerabilities. We list and briefly describe 10 of them below, in no particular order.
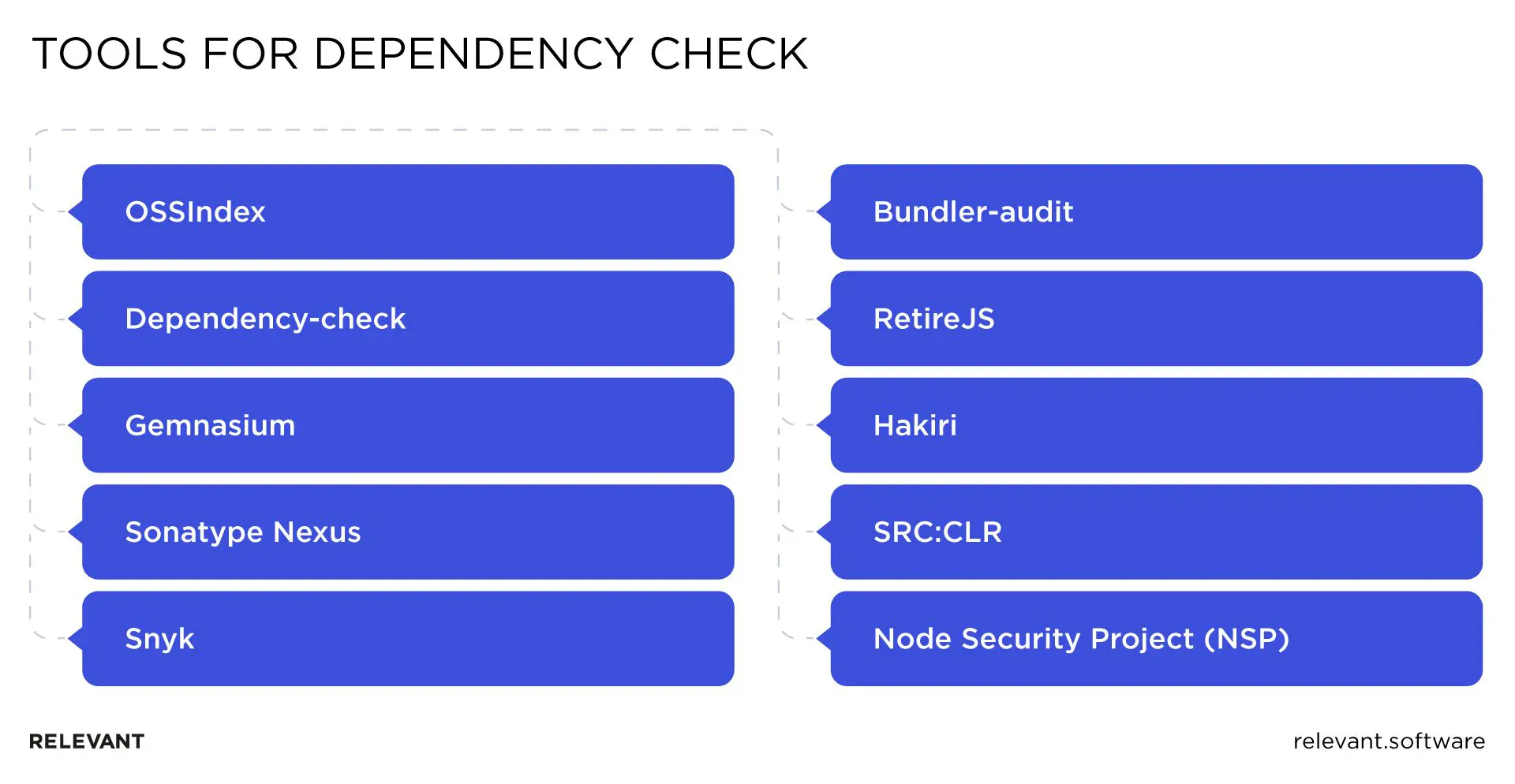
OSSIndex
OSSIndex from Sonatype covers Java, Javascript, Go, Python, Ruby, and .NET/C# ecosystem by extracting dependency information from public sources like Maven Central Repository, MSI, Nuget, Chocolatey, and NPM. This tool has a free vulnerability API allowing it to integrate with your tool kit easily.
The list of known vulnerabilities used by OSSIndex is currently retrieved from the NIST NVD (National Vulnerability Database from the National Institute of Standards and Technology) to cover the widest known range of potential issues. However, to update the known vulnerability base in real-time, OSSIndex developers plan to add an automated import for other databases, mailing lists, and bug-tracking tools soon.
Dependency-check
Dependency-check is yet another open-source product from OWASP. This command-line tool can work as a part of your build suite or as a standalone instrument. Working with Ruby, Java, JavaScript, and .NET, Dependency-check is a trustworthy and reliable choice for enterprise-grade development, which works directly with NIST NVD.
Gemnasium
Gemnasium is a proprietary SaaS product with several free starting plans and an internal database of vulnerabilities, updated daily from multiple sources. Nevertheless, forming advisories requires a manual check, and these are not published automatically. One of the major benefits of Gemnasium is its ability to test specifically selected combinations of dependency sets, instead of checking all of them, saving a ton of time and effort. Slack integration ensures your developers get immediate updates once an advisory is detected.
Gemnasium is currently a cloud-based product supporting Ruby, Python, PHP, NPM, and Bower. However, the plans for new features include building an enterprise-grade on-prem solution supporting Java and other languages.
Sonatype Nexus
Sonatype Nexus is an enterprise-grade suite of tools for repository/binary management, app building, dependency checking, and reporting. It was developed by the team behind Apache Maven and its Central Repository. It’s a feature-rich software suite covering a vast variety of platforms, from Java and PHP to .NET, Go, Ruby, Python, and Swift.
Nexus helps issue and enforce policies that prevent suspicious open-source components from entering your software delivery supply chain. It also provides integration with CI/CD tools, statistics visualization to identify MTTR and success metrics, expert guidance on compliant alternative versions, etc. Automated generation of Software Bill of Materials for every build, continuous monitoring for new vulnerabilities — this is just the tip of the iceberg that is Nexus.
Snyk
Snyk is a proprietary SaaS tool centered at checking JavaScript NPM vulnerabilities and dependencies based on NIST NVD and NSP. While it’s a relatively new guy on the block, it has already made a name for itself. In addition to detecting known JavaScript vulnerabilities in your open-source JavaScript code components, Snyk provides guided upgrades and custom-made patches to remediate them.
The main benefit of Snyk is that it helps scale successful vulnerability handling scenarios across all teams in an organization of any size. This way, it enables better collaboration and tighter GitHub integrations. Snyk’s development roadmap promises the release of runtime management tools for tight control and in-depth visibility of open-source JS modules in production environments.
Bundler-audit
Bundler-audit focuses on checking dependencies and vulnerabilities in Ruby projects. It’s an open-source command-line tool retrieving updates from RubySec (specialized Ruby vulnerability database) and NIST NVD.
RetireJS
RetireJS is a community-backed open-source JavaScript dependency checker. It has plugins for Firefox, Chrome, Gulp, Burp, ZAP, and Grunt. Being user-friendly, RetireJS also provides a site dependency checker in addition to software build monitoring. Any web developer can check if their websites are running JS components with known vulnerabilities. The tool retrieves vulnerability updates from NIST NVD and a bunch of specific JS blogs, bug-tracking systems and email lists. RetireJS project aims at improving collaboration between the authors of popular JS libraries and the rest of the community, so that the authors report freshly discovered vulnerabilities in their modules themselves.
SRC:CLR
Source Clear is another proprietary SaaS tool with a command-line interface, which provides many plugins for IDE management, handling deployment tools for various platforms and frameworks, and even more useful features. One of the most crucial between them is the “vulnerability methods identification” — a check whether the vulnerable dependency discovered is currently used in your app. It helps diminish the number of false positives, allowing your Dev teams to concentrate on dependencies that matter. Source Clear leverages NIST NVD and several other databases and mailing lists to update its dependency database.
Node Security Project (NSP)
This is the main dependency checker for Node.JS and NPM dependencies. The information is retrieved from NIST NVD and an internal database updated from NPM module scans. The motto of this platform is making dependency security an integral part of the SDLC. This way, NSP aims to provide a suite of tools for enabling security dependency checking, alerting, and remediation to empower your development teams and allow seamless software delivery.
Method 2: Manual checks
Manual checking requires more effort, but it’s a great exercise for your developers. It gives them a deep understanding of transitive dependencies within open-source components they use, as well as an acquaintance with the vulnerability databases. This process can be boiled down to three steps.
- Collecting transitive dependencies. Most popular build managers have commands for collecting dependencies within your projects.
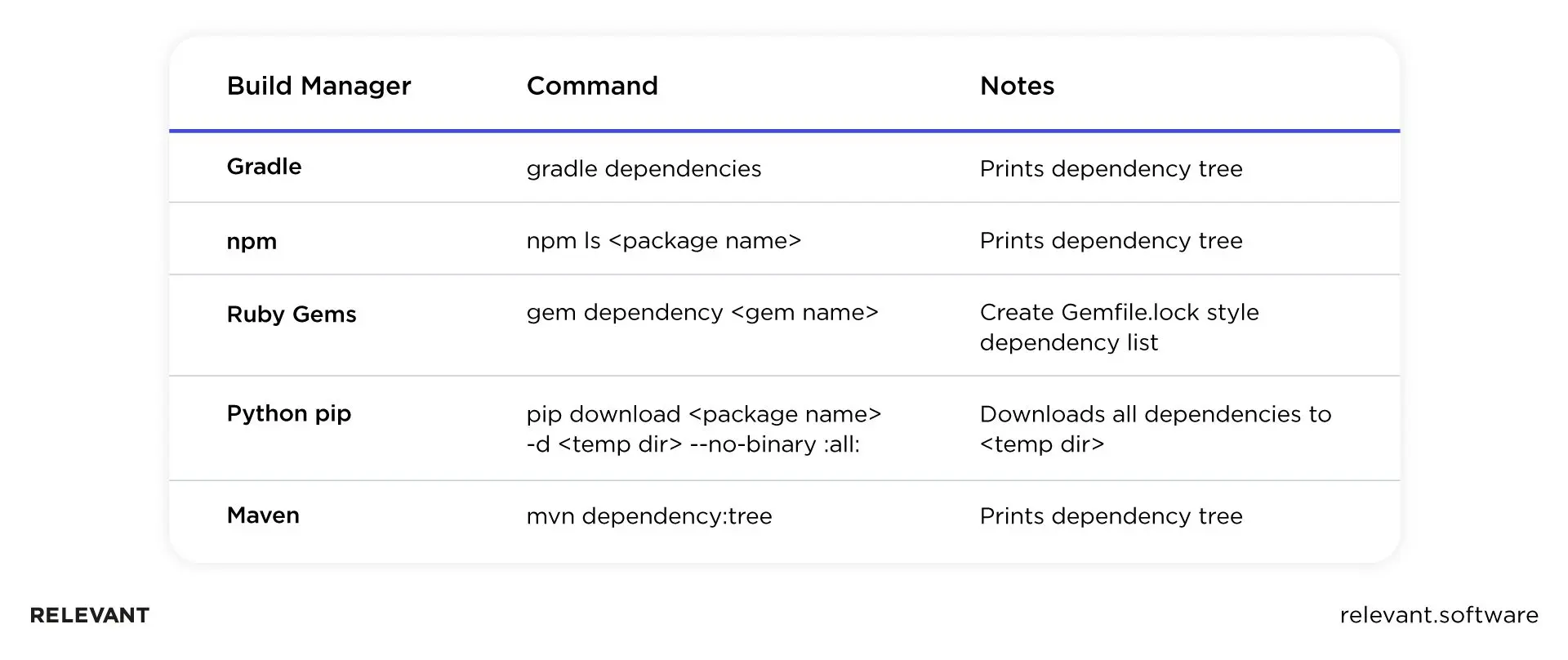
Search for known vulnerabilities for these dependencies. There are multiple databases of known vulnerabilities. They’re used by the tools we mentioned above, but your developers should know how to utilize Mitre’s Common Vulnerabilities and Exposures, Ruby Advisory DB, OSS Index, and other public sources.
Remediate these vulnerabilities by patching the code, upgrading to the latest version of this library or framework. Developers rarely report vulnerabilities in their code, which means public exposure and extra effort to fix the issues. Therefore, in many cases, such fixes go under the radar, and you must actively monitor them to stay updated. This can be done using the commit watcher tool, which can audit code commits and search for specific comments and descriptions, based on user-defined rules and search queries.
Summary
As you can see, there are paid and open-source tools for checking your code dependencies for vulnerabilities — or your development teams can do this manually. While the latter variant is more time- and resource-intensive, it’s a great way of educating your developers, so they make fewer mistakes when using third-party code components, check for vulnerabilities, and remediate them at once. Should you prefer your developers to concentrate instead on the software delivery process, please use any of the 10 dependency checking tools listed above.
Alternatively, you can delegate this task to a trustworthy technology partner like Relevant Software, which will perform the code audit and help your developers remove the potential security breaches. Should you have any questions or need any assistance with this task — we’re always ready to help!


Hand-selected developers to fit your needs at scale! Let’s build a first-class custom product together.

