IoT Device Security Concepts and Best Practices
Updated: June 5, 2025
The IoT device security concepts are not limited to the gadgets we carry in our pockets or use to scroll through web pages. We are now part of a world where appliances as common as refrigerators and as specialized as office security systems are online entities, forming a vast network known as the Internet of Things (IoT). Yet, amidst the convenience and advancements, there’s a critical aspect that’s often overlooked — the security of these systems.
It’s essential to recognize that these smart devices, which seamlessly blend into our daily routines, are potential gateways to our private information. Compromised IoT devices are more than just minor inconveniences; they can serve as conduits to sensitive data. The consequences extend beyond personal privacy in the enterprise and healthcare industries, where security breaches can have dire consequences.

We provide companies with senior tech talent and product development expertise to build world-class software. Let's talk about how we can help you.
Contact usAcknowledging these risks is the first step. The next and most crucial is fortifying these devices against threats. This guide will not only emphasize the significance of securing our interconnected tools but will also provide actionable strategies to fortify the devices at the heart of the Internet of Things.
Table of Contents
Why IoT Device Security Can’t Wait
So, why is IoT devices security such a big deal? It’s simple. Without strong defenses, any IoT device can be hacked, putting user data and entire systems at risk. As more devices connect, the attack risk grows, and network safety depends on the security of the weakest link. Securing IoT isn’t easy because:
- We often don’t know what devices are connected.
- Many devices lack strong, updatable security.
- They produce tons of data that’s hard to monitor.
- Different teams manage different devices without a unified approach.
- Devices vary widely, complicating consistent protection.
- Integrating IoT security into overall IT strategies is tough.
- Plus, almost all IoT data is sent without encryption, which is a major risk.
Every IoT device is a door that might let hackers in, including the ones we don’t even know are there. They can be hijacked and used in large-scale cyberattacks like DDoS. But, unlike regular IT gadgets, many IoT devices are hidden in networks, so we can’t always protect them similarly.
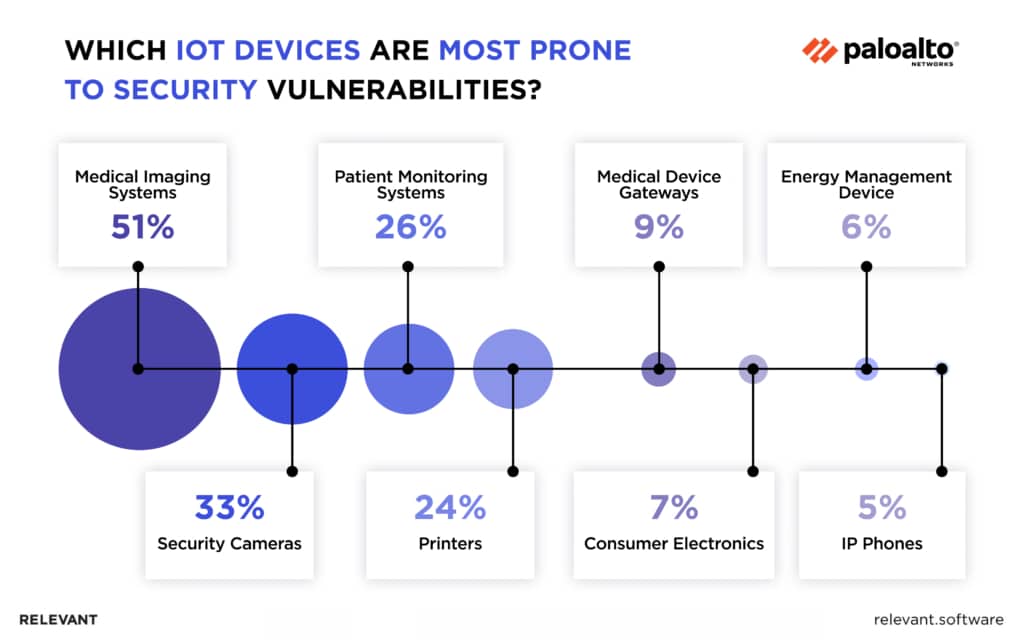
Source: Paloaltonetworks
Fundamental IoT Device Security Concepts
Several key concepts behind IoT device security are vital to understand if we want to keep our interconnected gadgets secure.
Device Identity
The cornerstone of IoT device security begins with something called “device identity management.” Just like every person has a unique identity, every device in the IoT landscape must have a unique identifier. This uniqueness is not just a fancy feature; it’s essential for maintaining the integrity and trustworthiness of the network.
- Why Unique Identifiers Matter? Think of it this way: if every device on your network is uniquely identifiable, it becomes easier to track their activities, understand their roles, and, most importantly, spot anomalies. When a device begins to behave unusually, identifying it accurately makes it easier to pinpoint the problem.
- Implementing Certificates and Keys: This is where device digital certificates and keys come into play. They are like digital passports and security clearances for devices. Implementing them means each device carries a verified credential, proving its legitimacy and defining its access rights. It’s like having a tightly controlled guest list for a high-profile event. You know exactly who’s coming in, and you’ve pre-approved their access.
Data Encryption
Encryption is the heavy-lifter in IoT security. It’s the process that keeps data confidential and tamper-proof, both while it’s stored (‘at rest’) and when it’s being sent across networks (‘in transit’).
- Why Encrypt Data? The reasoning is straightforward yet powerful. Encryption transforms data into a form that is unreadable to anyone who doesn’t have the key to decode it.
- Common Protocols in IoT Devices: Several encryption protocols are standard in IoT devices, each with its strengths. Protocols like TLS (Transport Layer Security) and AES (Advanced Encryption Standard) are commonly employed to protect data in transit. For data at rest, encryption methods like XTS-AES or RSA are often used. The goal is to ensure that even if data falls into the wrong hands, it remains undecrypted and useless to the interloper.

Secure Boot and Firmware Integrity
When we delve into the arena of IoT device security, “Secure Boot” and “Firmware Integrity” play pivotal roles. They are essential shields protecting your devices from being compromised right from the moment they power up.
- Understanding the Boot Process: It is the initial set of operations that a device performs when it turns on. It’s a critical phase because it’s the foundation on which the entire operating system stands. A compromised boot process is like building a house on shaky ground – everything that comes after is unstable.
- Threats to Consider: The threats here are real. Hackers can target this phase to inject malicious code, which then gets free rein over the device. That’s why the integrity of the boot process is non-negotiable.
- Ensuring Firmware Authenticity: When it comes to firmware — the essential software that runs your IoT devices — it’s critical to confirm its authenticity. Making sure the firmware hasn’t been altered is much like ensuring the ‘brain’ of your device is in top condition and hasn’t been compromised. We achieve this through methods such as cryptographic signing, which is a bit like a thorough ID check that confirms a person’s identity before they’re allowed into a high-security area. If the firmware doesn’t pass this strict verification process, it’s back to square one — it can’t be trusted.
Network Security
In the realm of connected devices, the importance of adhering to strict IoT device security protocols can’t be overstated.
- Why is it crucial? It boils down to ensuring that the lines of communication between your devices are locked down tight. Imagine each of your devices communicating over a private channel that is encrypted, like a top-secret conversation. No eavesdroppers, no interference — just a secure and private dialogue.
- Utilizing Advanced Security Measures: This is where advanced security measures come into the picture. Consider tools like VPNs, which create a secure tunnel for your data, much like an armored train transporting gold through a bandit-infested territory. Then there are firewalls, which serve as gatekeepers, turning away suspicious traffic like a discerning bouncer at a club. And let’s not forget intrusion detection and prevention systems — they’re the vigilant security guards monitoring for any hint of a breach, ready to shut down threats before they can cause harm.
By employing these sophisticated safeguards, you can bolster the fortitude of your IoT ecosystem against various threats, ensuring that your network stands firm in the face of potential cyber onslaughts.
Software Updates and Patches
In the vast, dynamic world of IoT, staying updated isn’t just good practice; it’s a crucial defense strategy. Let’s dive into why regular software updates and patches matter and the challenges faced in their deployment.
- Why Do Updates Matter? Think of software updates as the health check-ups we routinely need. Just as these check-ups prevent illnesses or detect them early, software updates address vulnerabilities that, if left unchecked, could compromise a device. Vulnerabilities are, unfortunately, a part of any software’s lifecycle. As new flaws are discovered, updates are the tool IoT developers use to fix them, ensuring devices remain resilient against potential security breaches.
- Patching: A Must, Not an Option: Patches are targeted software fixes for specific vulnerabilities. It’s like finding out there’s a leak in your house and promptly sealing it before any more damage occurs. The quicker these patches are deployed, the better protected the device is from potential threats.
- Challenges in Deployment: While the logic behind updates is straightforward, the deployment can be complex. Why? Because in the IoT ecosystem, devices come from various manufacturers, run on different platforms, and operate in diverse environments. Ensuring that one patch applies equally to all these devices and functions as expected is no easy task. Additionally, every update carries a risk of incompatibility or new IoT devices security issues arising. Addressing these requires thorough IoT device security testing, reliable delivery mechanisms, and sometimes even user education.
Physical Measures
While we’re busy focusing on viruses and hackers, we can’t forget about the actual physical devices in our homes, offices, and public spaces.
- Guarding Against the Tangible Threats: It’s a bit like home security. You wouldn’t leave your windows wide open when you leave for vacation, right? Similarly, IoT devices need protection from tampering or, worse, being stolen.
- Making Devices Tamper-Proof: Have you ever seen those “warranty void if removed” stickers? That’s one way to know if someone’s been fiddling with your stuff. IoT devices can have similar features to tell you if they’ve been tampered with, alerting you to any funny business.
API Security
APIs, or Application Programming Interfaces, serve as bridges, allowing different software components to communicate. However, just as any bridge can become vulnerable if not well-guarded, APIs too can be susceptible.
- Robust Security Controls: One doesn’t need to venture deep into technical weeds to grasp the principle: an unsecured API is like an open door in a fortified castle. Effective security controls ensure that this door is not only locked but also regularly inspected for potential weak points. This involves methods like encryption, monitoring, and routinely testing APIs against potential breaches.
- Common Vulnerabilities and Their Mitigation: Several IoT device security issues tend to crop up with IoT APIs. Among them are lack of proper authentication, exposed sensitive data, and poor error handling. Addressing these requires a mix of proactive measures, like ensuring robust endpoint security, and reactive steps, like timely patches for known vulnerabilities.
Access Control and Authentication
The realm of IoT is vast, and with it comes the challenge of ensuring that every device and user is precisely who they claim to be. Access control policy and authentication stand as the gatekeepers in the security of IoT devices.
- Multi-factor Authentication and Password Protocols: It’s no longer sufficient to rely on simple username-password combinations. Multi-factor authentication, which might involve something a user knows (password), something they have (a token or phone), and something they are (biometrics), offers a layered defense against unauthorized access. Complementing this with strong password policies, such as mandatory periodic changes and complexity requirements, further bolsters device security.
- Limiting Access: Just as not everyone should have the keys to every room in a building, not all users or services should have unrestricted access to IoT devices. It’s vital to ensure that only those who truly need access get it, and even then, only to the necessary levels. This approach minimizes potential points of entry for malicious actors.
Common IoT Device Security Threats
In the evolving world of IoT, awareness of potential IoT security challenges is not just advisable — it’s crucial. Here, we’ll dissect some of the common risks that IoT devices face, offering you a clear understanding of how to safeguard your connected ecosystem better.
Malware and Botnets
Malware, in the context of IoT, is malicious software that can hijack your device for nefarious purposes. What’s more concerning is the creation of botnets — a network of infected IoT devices. These botnets can launch coordinated attacks or facilitate other illegal activities without the device owner’s knowledge.
- How they operate: Imagine each IoT device as a soldier. Alone, it might not pose much threat. But when orchestrated in unison under a hacker’s control, they form an army capable of wreaking havoc. These botnets can spread malware, steal data, or execute coordinated attacks on other networks.
- Countermeasures: To prevent your devices from becoming part of a botnet, regular firmware updates are critical. Also, employ network monitoring to detect unusual activities, indicating that a device might be compromised. Strong, unique passwords for each device and network segmentation can also reduce the risk of widespread infections.
Denial of Service (DoS) Attacks
Think of DoS attacks as someone bombarding your IoT gadgets or network with so much traffic that they just can’t cope, kind of like clogging up a machine by overloading it with tasks.
- Here’s how to picture it: Your IoT device is like a diligent office worker who’s great at their job. But when a DoS attack hits, it’s as if a mob of customers floods the office, demanding attention all at once. The worker gets swamped, and the real requests can’t get through, leading to a mess and downtime.
- Prevention strategies: To fend off these digital onslaughts, it’s all about controlling the flow of data. Firewalls and intrusion prevention tools act like bouncers, keeping the shady traffic out. And just in case trouble starts, having a solid game plan and a robust network can soften the blow.
Physical Attacks
Now, for the physical side of things — it’s not just the stuff of spy movies. Actual hands-on tampering with your IoT devices is a big threat.
- Let’s break it down: Physical attacks on devices mean actually getting hands-on with the gadget to mess with it directly. Although, in theory, any secure processor could be at risk, pulling off this kind of attack typically demands a lot of costly equipment and a hefty time commitment to achieve anything significant. These attacks are hands-on and often leave a mark, altering the device’s physical components in ways that can’t be undone. Pulling off a successful physical attack is like completing a complex heist, where precise actions must be taken at just the right moments. Attackers might aim to dig out confidential info like encryption keys from the processor, mess with the device’s original design, or even dissect the chip to understand how it was put together.
- So, how do you guard against that? Keep those devices under lock and key, literally or figuratively. Use gear that’s not easy to mess with. In places where it’s hard to keep track of what’s going on, encrypting your device data and ensuring devices only boot with trusted software can keep your information and transactions safe even if someone gets their hands on your device.
IoT Device Security Best Practices
Now, let’s dive into some top-notch practices to secure your IoT devices, especially focusing on solid password management and clever network design.

Strong Password Policies
- Creating and Managing Secure Passwords for IoT Devices: When you’re setting up passwords for your IoT devices, think of them as your first defense. Each device needs a password that’s not just unique but also complex. Steer clear of passwords that are simple or predictable – that’s practically inviting trouble. Mix it up with upper and lower case letters, numbers, and symbols. The more complicated and lengthy it is, the better.
- Implementing Multi-Factor Authentication (MFA): If you can, add an extra layer of protection with multi-factor authentication. This might mean a code sent to your phone or your fingerprint – anything that adds another hurdle for anyone trying to sneak in. Even if your password does fall into the wrong hands, MFA makes it much tougher for them to access your device.
Network Segmentation
- Isolating IoT Devices from Critical Networks: Think of network segmentation as dividing a building into different rooms, each with its own secure lock. By segmenting your network, you’re essentially putting IoT devices in their own separate space, away from the really sensitive parts of your network. If a device gets compromised, the damage can be contained and won’t spread everywhere.
- Benefits of Segregating IoT Device Traffic: By segregating IoT device traffic, you can more easily monitor and control the flow of information. It also simplifies identifying unusual patterns that may indicate a security breach. Another benefit is the reduced risk of lateral movement of threats across the network. If one segment is compromised, others remain protected, acting as a dam stopping the flow of potential threats across your network.
Regular Security Audits and Testing
- Сonsistent and thorough security audits: While new devices bring innovative solutions to our lives, they also, unfortunately, introduce new vulnerabilities. Therefore, security audits become indispensable. These audits don’t just provide a current snapshot of device health; they pave the way for future security enhancements.
- Penetration testing: Often referred to as ethical hacking, penetration testing dives deep into devices, seeking to identify potential weaknesses before adversaries do. By employing a hacker’s mindset, albeit with a protective intent, experts can root out vulnerabilities, from the obvious to the obscure, ensuring robust security for IoT devices.
Privacy Considerations
- Privacy by Design: It’s about weaving privacy into the very fabric of an IoT device from the initial sketch to the final product. Manufacturers who take this path not only safeguard their users but also set a standard in the industry for responsible design.
- Transparency: Users deserve to understand exactly what happens with their data — straightforward, no legalese. They should feel in control, with simple tools to adjust their privacy settings as easily as they would set an alarm.
- Data minimization: Just as you wouldn’t take more than you need from someone’s home, IoT devices should only gather the data essential for their function — nothing more. It’s a respectful nod to privacy, acknowledging that every byte of data is personal.
- Secure data storage: Imagine a vault within a vault. Even if someone breaks through the outer defenses, the core remains impenetrable. Data encryption and anonymization act as that inner sanctum, keeping users’ identities not just out of reach but out of recognition — because everyone deserves peace of mind, knowing their personal information stays private.
IoT Device Security Concepts: Final Words
Now, you’ve seen just how intricate and essential the security on IoT devices is in the ever-growing IoT world. It’s not just about setting up defenses; it’s about weaving IoT device security into our daily routine.
Here’s where our approach stands out – and it’s not just on standby, reacting to threats. Our IoT developers team is all about staying a step ahead and proactively safeguarding the IoT architecture. We’ve got a track record of thinking outside the box, tailoring our IoT device security solutions to fit each unique IoT setup.
So, when you team up with us, it’s more than just getting a cybersecurity service. You’re signing up for a partnership that’s all about forward-thinking and custom solutions. We’re here to ensure your IoT world is not only connected but also comprehensively protected.
Our core services:
Do you want a price estimate for your project?
Do you know that we helped 200+ companies build web/mobile apps and scale dev teams?
Let's talk about your engineering needs.
Write to us