Ultimate HIPAA Compliance Checklist for 2025: Simplified and Effective
Updated: June 5, 2025
Beyond thousands of dollars in fines, the risks of non-compliance with HIPAA are deeper and more long-term. This kind of oversight can cause severe legal consequences, but perhaps more importantly, it can damage your reputation and the very trust and confidence your patients place in your care. That’s why we’ve put together a detailed HIPAA compliance checklist to help you avoid these costly and frustrating mistakes.
As experts in healthcare software development whose software is also subject to HIPAA regulations and compliance, we know that it may feel like a daunting chore. But to state the obvious, nobody wants to get on the HIPPA Wall of Shame list. For that reason, we’ll review the fundamentals of maintaining HIPAA compliance, share practical advice, and provide a step-by-step checklist.

We provide companies with senior tech talent and product development expertise to build world-class software. Let's talk about how we can help you.
Contact usTable of Contents
HIPAA Compliance: Overview
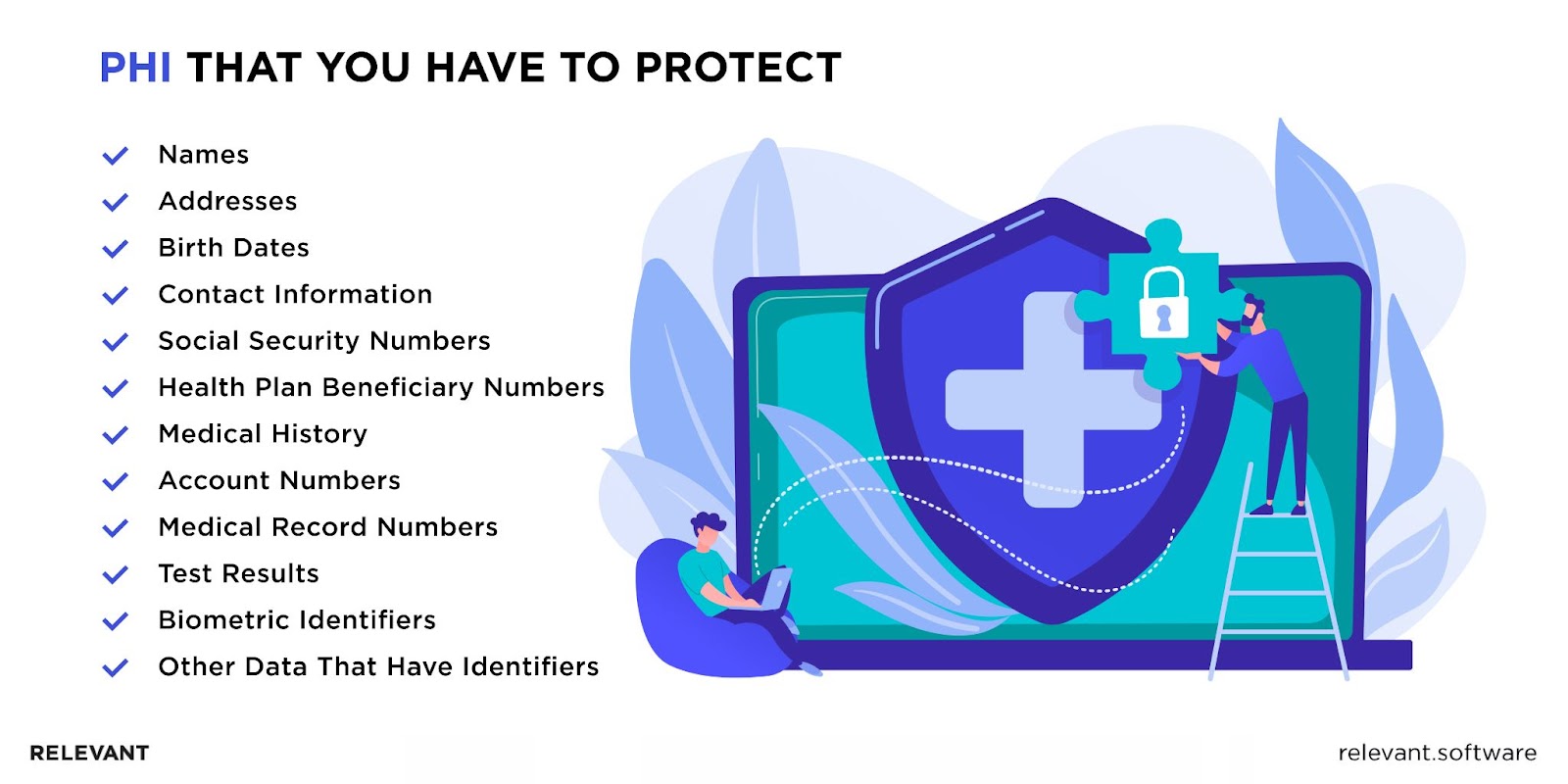
HIPAA, or the Health Insurance Portability and Accountability Act, is a US federal law that outlines rules to prevent the disclosure of sensitive patient health information. Following these regulations for every healthcare organization that deals with, manages, or shares protected health information (PHI) is a must. PHI includes any information in a medical record that can be used to identify an individual, such as names, Social Security numbers, and addresses, along with diagnosis, treatment, and test results.
Fines for violating HIPAA requirements range from $137 to almost $70,000 per violation, depending on the level of negligence (with a maximum of $2 million per year for repeated violations), to criminal charges in serious cases. For example, in 2023 alone, healthcare companies have paid over $2 million in penalties due to non-compliance.
| Minimum penalty per violation | Maximum penalty per violation | Limit for identical violations in the same year | |
| Unaware of violation | $137 | $68,928 | $2,067,813 |
| Reasonable cause and not willful neglect | $1,379 | $68,928 | $2,067,813 |
| Willful neglect but was corrected within 30 days | $13,785 | $68,928 | $2,067,813 |
| Willful neglect and not corrected within 30 days | $68,928 | $2,067,813 | $2,067,813 |
Source: Federalregiste
Whoever uses PHI – business associates, healthcare providers, or other covered entities – should make sure they meet the HIPAA compliance requirements checklist. Some of its key points are privacy and security rules. What’s important here is to understand that it’s an ongoing process of refining your organization’s security practices, policies, procedures, and technical safeguards.
Who Needs to be HIPAA-Compliant?
How to understand whether your organization falls under a mandatory HIPAA compliance checklist? In simple terms, if your work is connected to healthcare in any capacity and you have access to or process PHI, you must be compliant. Yet, not every organization must meet the same requirements to ensure compliance.
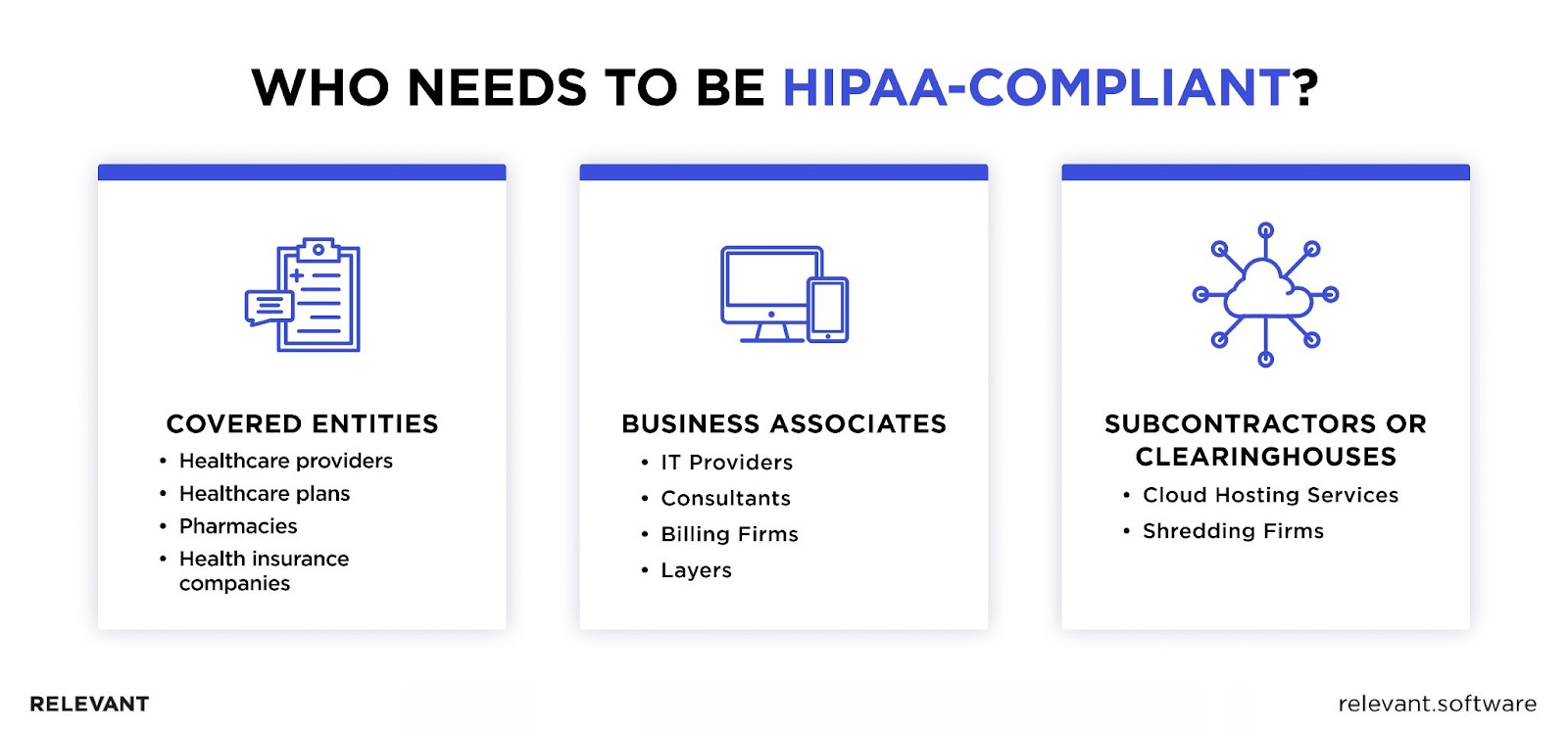
There are three types of establishments that must conform to all or some of its rules:
- Covered entities are all organizations and individuals that create, gather, or electronically transfer PHI. This category primarily refers to healthcare providers and health plan providers who are responsible for meeting all standards.
- Business associates (BAs) are any individuals or organizations that provide services to a covered entity and have access to PHI. This category involves IT providers, consultants, billing firms, and other businesses that, in one way or another, collaborate with healthcare companies. Under the Omnibus Rule, BAs must comply with certain Privacy and Security Rules.
- Subcontractors who are hired by BAs to assist with specific tasks. They must protect any PHI they deal with in the same way as the business associate, which includes maintaining security measures and reporting any PHI breaches.
HIPAA Compliance Checklist for 2025
So, what is a HIPAA compliance checklist, and why do you need one? It will help your company understand how to create necessary administrative, technical, and physical safeguards to protect your PHI. Here’s a quick 10-step HIPAA compliance checklist that covers everything you need to know to get your organization compliant.

Establish Security Management Standards
The privacy officer is a key figure who will help you lead this process, manage your compliance plan, and make sure you follow Privacy and Security rules. It’s vital to document everything – every step you take to protect patient info should be written down. Apart from bringing internal clarity, documentation is one of the parts of the HIPAA compliance checklist. Think of it as the backbone of your HIPAA compliance infrastructure, keeping everything in check.
Assign Responsibility for HIPAA Compliance
Getting the HIPAA compliance checklist right is easier when one person or department takes charge because it puts all the tasks and rules under one roof. This helps avoid confusion and ensure that nothing gets overlooked, while the whole compliance process becomes easier to manage and keep track of.
Develop a HIPAA Compliance Management Strategy
Here, we mean that you should make the HIPAA compliance checklist a part of your everyday organizational plans. Arrange regular staff training on rules, establish clear data privacy protocols, and routinely assess risks and vulnerabilities. This way, protecting PHI becomes a natural part of what you do, keeping you up with regulations.
Conduct HIPAA Risk Evaluations
Running a HIPAA risk assessment is one of the main requirements for compliance that will help you find any weak spots and vulnerabilities in how you handle patient data. That said, you should not only meet the HIPAA compliance software checklist but also ensure physical and admin protections are in place and function correctly. And if you spot any gaps or issues, having a corrective action plan is the right way to fix them fast and without any panic.

Ensure IT Infrastructure Meets Standards
Making sure your IT setup is HIPAA-ready and your PHI is stored safely covers two main areas: tech and physical security. On the technical side, you must use strong encryption and tight access controls at all times and at the bare minimum to protect patient data. As for physical safeguards, you should take measures to secure your offices and equipment that store PHI. For example, you can use key card access systems and cameras to control and monitor who has physical access to sensitive information.
Maintain PHI Handling Technology
Keeping your healthcare software systems for processing and sharing patient data up to date and functioning correctly should be a critical item on your HIPAA compliance security checklist. Because, let’s face it, outdated technology is the same as leaving the backdoor open. Cybersecurity services and regular updates close the gaps in software security that hackers might exploit, keeping your systems and PHI defenses strong and your compliance on point.
Investigate Violations
If an incident of PHI unauthorized use or disclosure occurs, you should investigate the reason behind it and what went wrong. While we often think of external breaches or hacks, most issues actually caused by internal security oversights or negligence. Upon determining the cause of the infraction, tighten controls and improve policies to avoid similar incidents in the future.
Record Violations and Remediation Plans
Maintaining a detailed log of any violations and the steps your company took to resolve them is essential for two reasons. The first and most obvious one it’s a part of the HIPAA compliance checklist. The second is having all HIPAA-related activities recorded in one place helps keep things clear and comes in handy if there’s ever a breach. For every issue you find, outline a plan and a timeline to fix it, especially after audits.
Understand the Four HIPAA Regulations
The HIPAA security compliance checklist outlines four basic rules for safeguarding the privacy and security of a patient’s medical information and understanding them is key to getting your business compliant. In short, the Security and Privacy rules are closely related, where the last one describes general PHI protections, and the Security rule specifies concrete measures for securing PHI. Then, we have the Omnibus rule that explains requirements for business associates and the Breach Notification Rule that requires companies to notify about PHI breaches.
Detailed Look at HIPAA Regulations
Let’s examine more closely what these four main regulations entail:
HIPAA Privacy Rule
Privacy rule protects patient data in any form (electronic, written, or verbal) and mostly applies to healthcare providers, insurers, and employer-sponsored health plans. All of them must follow the HIPAA privacy compliance checklist to ensure they use and disclose PHI only for valid reasons like care and billing.

To meet the requirements of the Privacy Rule, you should adopt security measures, provide a Notice of Privacy Practices to patients, and grant them access to their records, among other things. Adopting these practices will help you avoid common violations that include cases of PHI being shared improperly, not protected enough, or companies failing to issue privacy notices.
HIPAA Security Rule
The Security rule plays a major role in keeping electronic PHI secure. It requires healthcare organizations and their business associates to shield PHI against possible security risks, ensure it isn’t misused or shared improperly, and make sure their staff follow the rules. To do that, organizations need to meet every point in the HIPAA compliance checklist that implies technical protections as well as physical and administrative safeguards based on risk assessments.
HIPAA Omnibus Rule
The Omnibus rule, a recent update to the Act, broadened the range of organizations that need to follow the rules. Now, it’s not just healthcare providers who need to worry about compliance but also their business partners and subcontractors.
Although the majority of the regulations are not directly applicable to BAs, they still need to adopt some obligatory policies and safeguards of the HIPAA Privacy Rule compliance checklist. Since BAs and subcontractors may have access to some patient data, they should follow rules around the usage and disclosure of PHI, as well as the patient’s rights regarding their PHI. As a HIPAA-compliant healthcare software provider, we employ the latest security technologies and best practices to keep the highest standards of data privacy and security.
HIPAA Breach Notification Rule
Under the Breach Notification Rule, if a security incident occurs, organizations should report a breach to the Secretary of Health and Human Services within 60 days. They also should let all individuals whose PHI was compromised know about it within the same timeframe. And if it’s a big breach affecting more than 500 people, your organization should notify local media as well. It’s a crucial step in your HIPAA compliance checklist, where quick and clear communication can minimize the impact of security incidents.
HIPAA Compliance Checklist: Summary
Tackling HIPAA’s rules can feel like a huge task, and it’s so, indeed. But it’s important to stay on top of them because your oversight can be expensive. Sticking to your HIPAA compliance checklist for 2024 involves following many of the same principles as in last years. And as you work to implement cybersecurity measures and internal PHI handling policies but have difficulties, don’t stress. You shouldn’t do it alone.
For over a decade, Relevant Software has been providing healthcare software development services to help organizations achieve and maintain HIPAA compliance. So, if you plan to build medical software that must be compliant with industry regulations or need some IT consultation on this subject, contact us to do that with ease and confidence.
Our core services:
Do you want a price estimate for your project?
Do you know that we helped 200+ companies build web/mobile apps and scale dev teams?
Let's talk about your engineering needs.
Write to us