Mobile Application Security Testing: Is Your App Safe?

What do you think about how vulnerable your mobile app is to mobile use? If mobile application security testing isn’t embedded in your development lifecycle, the answer is clear: very.
Every day, cybercriminals exploit unsecured APIs, weak encryption, and poor authentication —often before businesses even realize they’ve been compromised. More than 95% of nearly 6.500 popular mobile apps fail to meet the OWASP MASVS (Mobile Application Security Verification Standard), leaving user data exposed to breaches. Despite these warnings, many organizations prioritize speed over security, launching applications without rigorous security testing —a decision that leads to data leaks, financial losses, and compliance violations.
from 25 countries outsourced software development to Relevant
We provide companies with senior tech talent and product development expertise to build world-class software.
How can businesses prevent these risks before they become costly disasters? This guide from Relevant Software’s cybersecurity experts explains how to proactively secure mobile applications through comprehensive application testing services and security assessments.
What is mobile application security testing?
Every mobile app connects with users, networks, and back-end systems—each creating a potential attack surface. Mobile app security testing detects vulnerabilities before cybercriminals exploit them, thereby ensuring the integrity of secure applications. Unlike functional testing, which verifies app features and expected behavior, security assessments uncover weaknesses in:
✔ Authentication (password policies, multi-factor authentication)
✔ Encryption (data at rest & in transit security)
✔ API security (broken authentication, data exposure risks)
✔ Data storage (insecure local storage, improper access controls)
✔ Communication protocols (network security, SSL/TLS configurations)
Here’s a table to clearly differentiate security testing from general app testing:
| Testing Type | Objective | Focus Areas | Key Techniques | Key Risks if Ignored |
| Functional Testing | Validates app features and expected behavior | UI/UX consistency, business logic, input validation | Unit tests, integration tests, end-to-end testing, user acceptance testing (UAT) | Broken functionalities, poor user experience, higher defect rates post-release |
| Performance Testing | Assesses app speed, stability, and resource efficiency | Load handling, memory usage, response times, concurrency limits | Load testing, stress testing, spike testing, endurance testing | Slow response times, crashes under high traffic, excessive battery/CPU usage |
| Mobile App Security Testing | Identifies and mitigates security vulnerabilities that could lead to exploitation | Authentication, encryption, API security, secure data storage, runtime protection | Static (SAST), Dynamic (DAST), Interactive (IAST) security testing, penetration testing, fuzz testing | Data breaches, API exploitation, unauthorized access, compliance violations |
To standardize testing mobile applications for security vulnerabilities, cybersecurity professionals rely on the OWASP Mobile Security Testing Guide (MSTG) —a comprehensive framework that defines industry best practices for mobile app assessments and penetration tests.
The MSTG establishes methodologies for evaluating security across iOS and Android applications, with static (SAST), dynamic (DAST), and interactive (IAST) analysis. It provides detailed checklists, attack scenarios, and remediation strategies to help businesses identify, exploit, and mitigate web application vulnerabilities before attackers do. The framework addresses data storage security, authentication and session management, cryptographic implementation, network communication security, and API protection, which ensures that security measures align with real-world threat models.
Applying MSTG principles allows businesses to systematically detect security gaps, meet compliance standards like GDPR and PCI DSS, and reinforce mobile application defenses before deployment. OWASP MSTG-based methodologies help reduce breach risks, build trust in mobile applications, and strengthen resilience against modern cyber threats.
Why mobile application security testing is critical
The data below proves that mobile application security tests are no longer optional—they are critical for business survival.
Growing mobile security threats
Mobile applications process vast amounts of personal, financial, and corporate data, which makes them prime targets for cybercriminals. Relevant Software experts reveal critical threats that put businesses at risk:
- 60% of cyberattacks focus on mobile applications due to weak authentication and unprotected APIs.
- Over 75% of mobile apps contain at least one security vulnerability, exposing sensitive user data to exploitation.
- The average cost of a mobile data breach exceeds $4 million, with financial losses escalating due to compliance violations and reputational damage.
- Nearly 43% of cyberattacks target small and mid-sized businesses, yet only 14% are prepared to defend against them.
- AI-driven security testing reduces vulnerability detection time by 90%, enabling businesses to identify and fix security flaws faster.
Without mobile app security testing, businesses risk data leaks, financial fraud, and unauthorized access to user accounts. Proactive security testing for mobile applications is the only way to stay ahead of evolving threats, protect user data, and maintain business continuity.
Regulatory compliance and security standards
Failing to secure mobile applications creates more than just risks—it leads to compliance failures. Regulatory bodies worldwide enforce strict security and data protection laws that organizations must follow.
- GDPR (General Data Protection Regulation) – Requires businesses to implement security measures to protect user data or face fines up to 4% of annual revenue.
- HIPAA (Health Insurance Portability and Accountability Act) – Mandates secure management of healthcare data to protect patient privacy and maintain data integrity.
- PCI DSS (Payment Card Industry Data Security Standard) – Regulates mobile apps that process credit card transactions, requiring strict encryption and authentication measures.
- OWASP MASVS (Mobile Application Security Verification Standard) – Defines security benchmarks for mobile applications and details best practices for secure coding and mobile application security assessment.
- NIST (National Institute of Standards and Technology) – Provides cybersecurity frameworks that help organizations enforce mobile application security testing methodology.
Mobile application security testing tools help detect compliance gaps, enforce protections, and maintain regulatory adherence. Overlooking proper testing results in fines, lawsuits, and lost customer trust.
Business and user trust considerations
A single security breach can destroy years of brand reputation. Customers demand secure, trustworthy applications—and any sign of security negligence results in lost business.
- Change healthcare ransomware attack (Feb 2024): The BlackCat (ALPHV) group crippled Change Healthcare, caused nationwide disruption, led to a $2.87 billion loss for UnitedHealth Group, and forced a $22 million ransom payment while exposing critical healthcare data flaws.
- Snowflake data breach (May 2024): Hackers stole credentials to breach Snowflake, affected over 100 companies, including AT&T and Ticketmaster, exfiltrated billions of records, and demanded ransoms between $300,000 and $5 million.
- UK MoD data breach (May 2024): A cyberattack on a contractor’s payroll system exposed the personal and financial data of 270,000 UK military personnel, revealed third-party security flaws, and raised national security concerns.
Related – Cybersecurity in Fintech
Key security threats in mobile applications
Relevant Software experts uncover the most critical threats hidden in mobile applications, exposing how cybercriminals access systems without authorization, steal data, and cause financial harm. Awareness of these risks serves as the first step in their prevention.
Insecure data storage
Poor data storage exposes sensitive information to attackers. Many mobile applications keep user credentials, payment details, and personal data in plaintext, which allows hackers to retrieve information from local storage, cache, or unprotected databases.
Examples of exposed data
- Unencrypted storage – Sensitive records remain accessible without proper encryption, violating compliance standards.
- Session token exposure – Storing authentication tokens on devices enables attackers to hijack user sessions.
- Weak access controls – Insufficient restrictions allow unauthorized access to confidential user data.
- Insecure database configurations – Misconfigured databases lead to data leaks and exploitation by attackers.
Weak authentication and authorization
Weak authentication mechanisms open the door to unauthorized access, identity theft, and account takeovers. Many mobile apps rely solely on password-based authentication, which leaves users vulnerable to credential stuffing, brute-force attacks, and session hijacking.
Types of damages
- Unauthorized access – Attackers bypass weak authentication controls, and gain access to sensitive user data and administrative functions.
- Identity theft – Stolen credentials allow cybercriminals to impersonate users, which leads to fraudulent transactions and account misuse.
- Account takeovers – Exploited authentication flaws enable attackers to lock out legitimate users and assume full control over their accounts.
- Data exfiltration – Compromised authentication grants unauthorized access to databases, exposing personal, financial, and corporate data.
Unprotected API endpoints
APIs serve as the backbone of mobile applications, handling data exchange, authentication, and transaction processing. Attackers target insecure APIs to bypass security controls, steal user data, or gain admin privileges.
Common API exploits
- Broken authentication – APIs failing to validate user tokens leads to session hijacking.
- Lack of rate limiting – Attackers use automated scripts to brute-force credentials and extract bulk data.
- Improper input validation – Unchecked API requests allow SQL injection and data manipulation.
Reverse engineering and code tampering
Attackers decompile mobile apps to analyze source code, discover vulnerabilities, and modify app behavior. Weakly protected applications expose API keys, cryptographic functions, and internal business logic, which allows hackers to inject malicious code, bypass security controls, or create fraudulent app versions.
Risks of reverse engineering
- Banking and fintech applications often fall victim to code injection, leading to unauthorized transactions.
- Gaming apps experience modifications that manipulate in-game mechanics.
- Pirated app versions often include hidden malware and spyware.
Malware and phishing attacks
Mobile malware infections and phishing campaigns exploit user trust, manipulate app behavior, and steal confidential data. Attackers disguise malicious software as legitimate applications, tricking users into installing compromised versions.
Phishing attacks on mobile users
- SMS-based phishing (smishing) redirects users to fraudulent login pages.
- Fake app notifications prompt users to enter credentials into attacker-controlled platforms.
- QR code phishing (quishing) directs users to malicious websites that steal sensitive information.
Network-based attacks
Public Wi-Fi networks, unsecured connections, and weak encryption create opportunities for attackers to eavesdrop on mobile data transmissions, inject malicious payloads, or hijack user sessions.
Common network threats
- Man-in-the-middle (MITM) attacks intercept and modify data exchanged between a user and a server.
- SSL stripping attacks downgrade secure HTTPS connections to unencrypted HTTP, exposing sensitive data.
- Wi-Fi spoofing tricks users into connecting to rogue hotspots controlled by attackers.
Mobile application security testing types
So, how to secure mobile apps? Below, Relevant Software experts outline the key mobile application security testing types that strengthen app defenses.
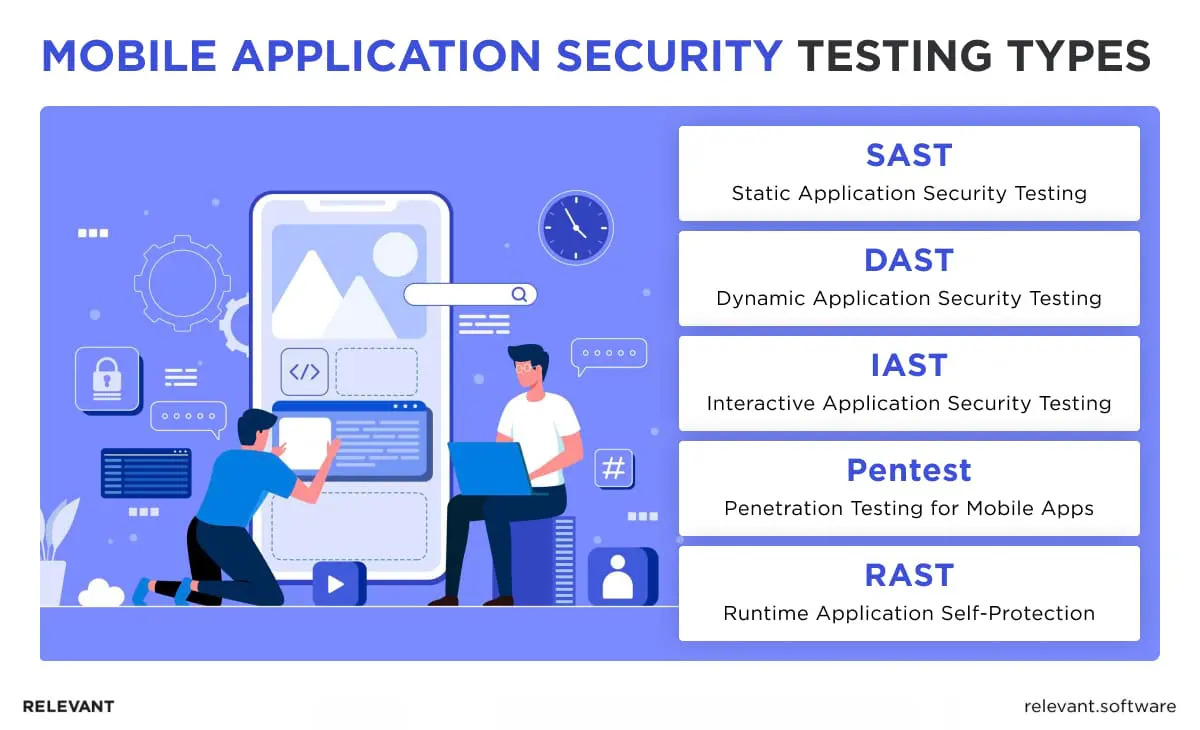
Static application security testing (SAST)
SAST examines an application’s source code, bytecode, or binary files without executing the program. This method identifies insecure coding patterns, hardcoded secrets, and weak encryption practices before deployment.
| Category | Details |
| Benefits of SAST | – Detects vulnerabilities early in development, reducing remediation costs.– Analyzes entire codebases without requiring a running environment. – Helps developers fix security flaws before attackers exploit them. |
| Limitations of SAST | – Generates false positives, requiring manual validation.– Lacks visibility into runtime behavior and API interactions.– Cannot detect configuration issues, authentication flaws, or business logic vulnerabilities. |
| Recommended tools | Mobile application security testing tools such as Checkmarx, Fortify, and SonarQube enable comprehensive SAST analysis, strengthening code security before launch. |
Dynamic application security testing (DAST)
DAST evaluates an application in a live environment, simulating real-world attack scenarios to uncover vulnerabilities in authentication, session management, and API security. Unlike SAST, DAST does not require source code access, making it suitable for black-box security testing.
| Category | Details |
| Benefits of DAST | – Evaluates applications in a live environment, identifying security flaws in real-time.– Assesses security risks without accessing the underlying code.– Uncovers authentication flaws, API weaknesses, and misconfigurations missed by static analysis. |
| Limitations of DAST | – Identifies vulnerabilities only after deployment, increasing remediation costs.– Cannot analyze internal logic or detect security flaws hidden in source code.– Focuses on technical vulnerabilities, which require manual review for complex attack scenarios. |
| Recommended tools | Burp Suite, OWASP ZAP, and AppSpider provide in-depth DAST analysis, exposing security weaknesses in running applications. |
Interactive application security testing (IAST)
IAST merges static and dynamic testing techniques, analyzing an application while it executes. Unlike SAST and DAST, which operate separately, IAST instruments the application to detect vulnerabilities in real-time.
| Category | Details |
| Benefits of IAST | – Analyzes applications both statically and dynamically for comprehensive security coverage.- Reduces false positives by verifying issues in real execution environments.- Identifies vulnerabilities during application runtime, enabling faster remediation. |
| Limitations of IAST | – Requires a live environment, which restricts early-stage tests.– Slows down applications due to deep runtime analysis.– Lacks full support for all programming languages and frameworks. |
| Recommended tools | Contrast Security, HCL AppScan, and Seeker IAST offer deep visibility into security flaws by integrating directly into the application runtime. |
Penetration testing for mobile apps
Penetration testing simulates real-world attack scenarios, identifying business logic vulnerabilities, API weaknesses, and authentication bypass risks. Unlike automated security tools, penetration testers use manual techniques to uncover security flaws that AI-driven tools may miss.
| Category | Details |
| Benefits of penetration testing | Identifies exploitable vulnerabilities before attackers do.Goes beyond automated scans to find human-exploitable weaknesses.Assesses authentication bypass risks and API misconfigurations. |
| Limitations of penetration testing | Requires manual expertise and customized attack strategies.More expensive than automated security testing.Unlike automated tools, penetration tests are not continuous. |
| Recommended tools | Kali Linux, Metasploit, and Core Impact enhance penetration testing with custom attack simulations. |
Common penetration testing techniques
- Reverse engineering – Decompiles mobile apps to analyze internal logic.
- Privilege escalation – Exploits misconfigurations to gain elevated access.
- Man-in-the-middle (MITM) attacks – Intercepts and manipulates network traffic.
- API fuzz testing – Sends malformed data to APIs, detecting unexpected system behavior.
For a detailed breakdown of penetration testing methodologies, refer to our guide on penetration testing for web applications.
Runtime application self-protection (RASP)
Unlike external security measures, RASP functions inside the app’s execution environment, blocking code tampering, unauthorized modifications, and runtime attacks without dependence on external monitoring tools.
| Category | Details |
| Benefits of RASP | – Identifies and neutralizes attacks as they happen, reducing response time.- Protects applications from reverse engineering, malware injection, and unauthorized modifications.- Secures applications independently of firewalls and intrusion detection systems.- Detects and blocks unauthorized API access and injection attacks in real-time. |
| Limitations of RASP | – Consumes system resources, which may slow down application performance.– Requires deep integration into application architecture, potentially delaying development cycles.- Some businesses hesitate to adopt RASP due to perceived complexity and compatibility concerns. |
| Recommended Tools | Imperva RASP, Waratek, and Jscrambler provide real-time security enforcement, protecting applications against runtime threats and unauthorized modifications. |
Security testing process for mobile apps
At Relevant Software, we specialize in mobile application security testing, that helps businesses identify vulnerabilities, mitigate risks, and strengthen security postures. Our experience spans fintech, healthcare, and enterprise software, ensuring compliance with GDPR, HIPAA, and PCI DSS while delivering secure, high-performance mobile applications.
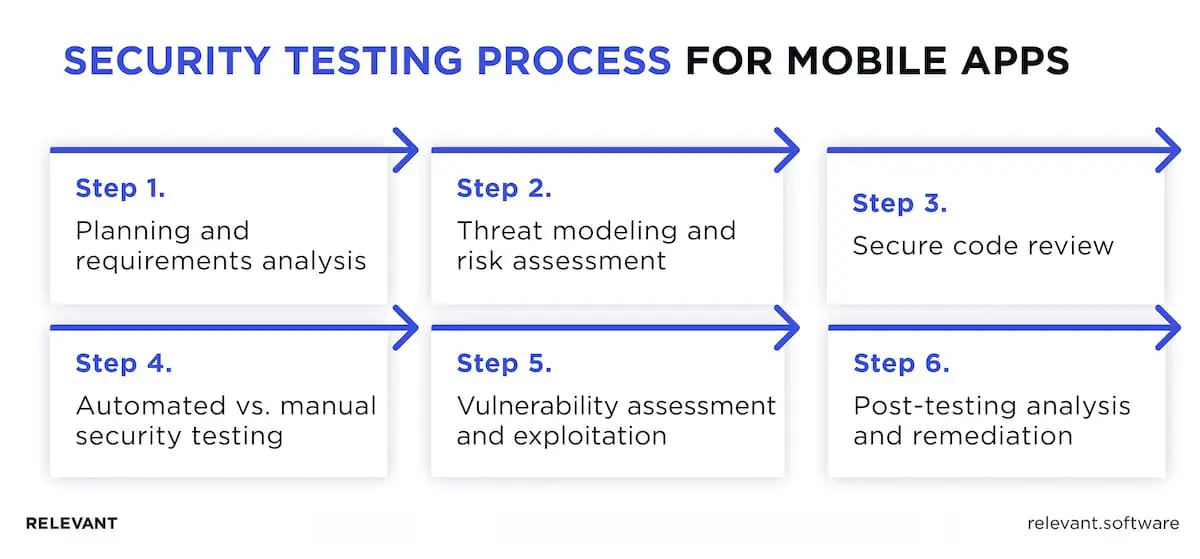
Step 1: Planning and requirements analysis
Effective security testing for mobile applications starts with clear objectives, regulatory requirements, and potential threat scenarios. The process includes:
- Defining the test scope to target source code, APIs, authentication mechanisms, or network security.
- Assessing critical assets such as user data, payment information, and proprietary business logic.
- Selecting the most effective security assessment methodology based on the application’s risk profile.
Step 2: Threat modeling and risk assessment
A structured threat model reveals potential attack vectors that impact mobile applications. This step includes:
- Mapping application architecture to identify entry points for attackers.
- Evaluating mobile-specific risks, such as insecure API calls, data leakage, and weak encryption.
- Classifying threats with risk-based frameworks, which include OWASP Mobile Top 10 and STRIDE.
Mobile application security assessment must incorporate threat intelligence and real-world attack simulations to build resilient architectures.
Step 3: Secure code review
Static analysis helps uncover security flaws before attackers exploit them. A thorough code review:
- Detects hardcoded credentials, weak encryption, and insecure API endpoints.
- Highlights unsafe patterns such as improper input validation and memory leaks.
- Uses mobile application security testing tools like Checkmarx, Fortify, and SonarQube to automate scans.
Step 4: Automated vs. manual security testing
A hybrid approach to mobile application security tests provides complete coverage, combining speed with deep analysis of complex risks.
Automated security testing
Automated testing enables rapid vulnerability detection through SAST, DAST, and IAST tools, efficiently identifying SQL injection, XSS, misconfigurations, and other common security flaws.
Relevant Software experts recommend this approach for large-scale applications that require continuous assessments, allowing rapid identification of known vulnerabilities.
Manual security testing
Manual tests uncover zero-day vulnerabilities, logic flaws, and authentication weaknesses that automated tools may miss. Cybersecurity professionals simulate real-world attack scenarios, assessing an application’s ability to withstand sophisticated threats.
The Relevant Software team considers manual tests essential for the security testing of mobile apps. This includes penetration assessments, threat modeling, and risk-based security evaluations, which provide deeper insight into business logic flaws and sophisticated attack scenarios.
Step 5: Vulnerability assessment and exploitation
Testing mobile applications for security vulnerabilities requires an offensive security approach to detect weaknesses before cybercriminals do. Key techniques include:
- API penetration tests to uncover broken authentication and exposed data.
- Privilege escalation attempts to evaluate gaps in role-based access control.
- Fuzz tests to identify unhandled exceptions and buffer overflow flaws.
Real-world case studies have shown that businesses fail to perform thorough vulnerability assessments of risk data breaches, financial losses, and regulatory penalties. Proactive testing remains the best defense.
Step 6: Post-testing analysis and remediation
Once teams identify vulnerabilities, they must:
- Prioritize threats based on severity, exploitability, and business impact.
- Develop the latest security patches while minimizing disruption to app functionality.
- Apply continuous test cycles to prevent recurring issues.
Relevant Software’s clients confirm that integrating mobile application tests into the Software Development Lifecycle (SDLC) helps detect vulnerabilities early, strengthen protections, and reduce breach risks. For insights into AI-driven assessments, explore our guide on how to test AI models and see how ML enhances mobile testing methodologies.
Best Practices for Securing Mobile Applications
To stay ahead of evolving threats, businesses must implement proactive security measures across authentication, data protection, network communication, and real-time monitoring. Below, Relevant Software’s experts outline the most effective strategies to fortify mobile applications, prevent breaches, and maintain user trust.
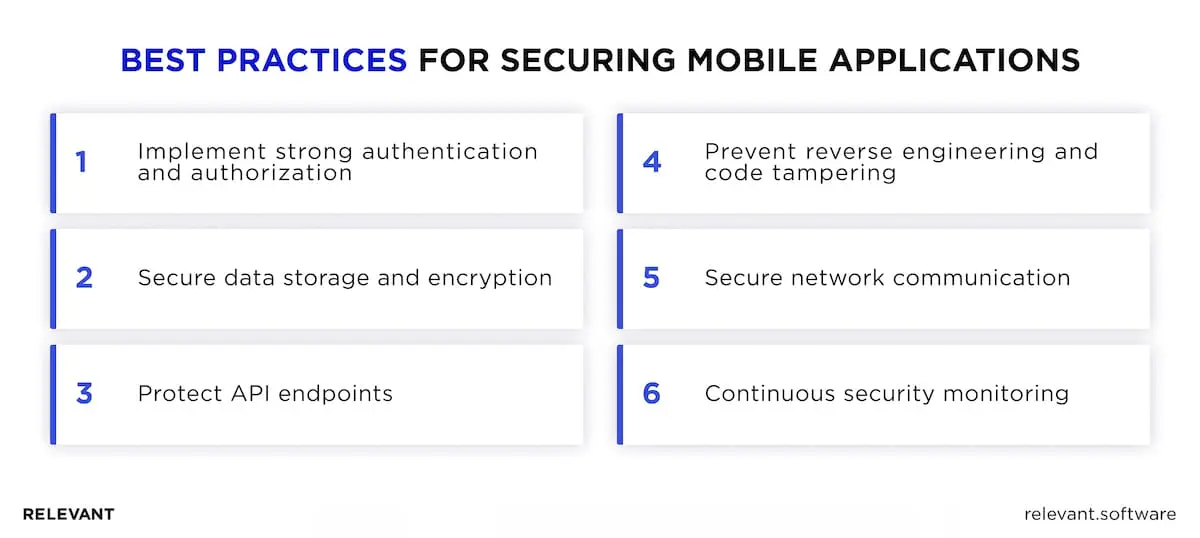
Implement strong authentication and authorization
Weak authentication exposes mobile applications to credential theft, unauthorized access, and account takeovers. Password reuse, short PINs, and the absence of multi-factor authentication create vulnerabilities that attackers exploit. Applications that rely solely on passwords without complexity rules or additional authentication layers remain highly vulnerable to brute-force attacks and phishing.
Solution: Stronger authentication requires strict password policies, longer and more complex credentials, and removal of default or weak passcodes. OAuth 2.0 and OpenID Connect enhance identity verification through secure, token-based authentication. Multi-factor authentication, biometric verification, and adaptive mechanisms reduce unauthorized access by confirming user identities beyond static credentials.
Secure data storage and encryption
Storing sensitive data in plaintext increases the risk of exposure if a device is compromised. Attackers can retrieve unencrypted information from local storage, application caches, or exposed database files. Misconfigured encryption libraries, hardcoded credentials, and weak cryptographic keys further degrade data security, which allows unauthorized access to confidential information.
Solution: Encrypting data at rest and in transit protects sensitive information from unauthorized retrieval. AES-256 encryption secures stored data, while TLS 1.3 ensures encrypted transmission between the application and backend servers. Secure key management solutions prevent unauthorized key access by storing cryptographic keys in hardware modules or protected enclaves, which reduces the likelihood of compromise.
Protect API endpoints
Unprotected APIs create attack vectors, exposing business logic, user data, and backend systems. Weak authentication, lack of rate limits, and improper access controls enable attackers to automate credential theft, extract bulk data, and manipulate API requests.
Solution: Secured API endpoints rely on API gateways to enforce authentication, monitor traffic, and mitigate denial-of-service attacks. Web application firewalls (WAFs) block malicious API calls and prevent injection attacks. Rate limits and strict access controls restrict unauthorized access and reduce abuse by validating requests against predefined security rules.
Prevent reverse engineering and code tampering
Attackers analyze mobile application code to uncover security flaws, extract sensitive logic, and inject malicious modifications. Reverse engineering allows unauthorized access to proprietary algorithms, encryption keys, and authentication mechanisms. Modified applications enable fraud, unauthorized transactions, and exploitation of premium features.
Solution: Obfuscated source code conceals logic, making it harder to analyze and manipulate. Anti-debugging techniques detect tampering attempts and block unauthorized code execution. Integrity verification mechanisms ensure applications run unmodified by validating signatures and checksums at runtime, which prevents unauthorized changes to application behavior.
Secure network communication
Unsecured network communication exposes sensitive data to interception, manipulation, and unauthorized access. Public Wi-Fi networks and unencrypted data transmissions create opportunities for attackers to execute man-in-the-middle (MITM) attacks, intercept login credentials, and manipulate transaction data.
Solution: Enforced SSL/TLS encryption protects data between mobile applications and backend servers. Certificate pinning prevents attackers from using forged certificates to intercept communication. Secure socket layer implementations and VPNs add additional layers of protection, which ensure confidentiality and integrity in network transmissions.
Continuous security monitoring
Threats evolve, rendering static defenses ineffective. Applications without real-time oversight remain exposed to zero-day exploits, unauthorized access, and malware. Delayed threat response increases data breach risks and financial losses.
Solution: Real-time monitoring detects anomalies and suspicious activity. Log analysis and alert integration with SIEM platforms allow rapid incident response. Regular audits and continuous assessments detect and resolve vulnerabilities before attackers exploit them.
AI and machine learning in security testing
Cyber threats evolve faster than traditional defenses, but AI-powered tools detect vulnerabilities before attackers exploit them. Unlike static models, AI adapts in real-time, detecting anomalies, zero-day threats, and suspicious behavior.
- AI-driven vulnerability assessment – Scans code and runtime environments to uncover weak encryption, misconfigurations, and API flaws.
- Automated penetration tests – Simulate attacks, and reveal logic flaws, privilege escalation risks, as well as authentication gaps.
- Behavioral analysis – Identifies account takeovers, credential theft, and malware by tracking user activity.
- Adaptive threat detection – Analyzes past attacks, refines models, and blocks future exploits.
Relying solely on outdated security measures leaves applications exposed. AI-driven assessments continuously refine security models, automate threat detection, and strengthen risk mitigation strategies, remain mobile applications resilient. As cybercriminals use AI to enhance their attacks, businesses must embrace AI-powered security to stay ahead, protect critical data, and safeguard long-term success.
Secure your mobile application with Relevant
One overlooked vulnerability is all it takes to cripple a business, expose sensitive user data, and erode years of customer trust. Attackers move fast—faster than ever—targeting weak authentication, unprotected APIs, and flawed encryption before businesses even detect a breach. Will your app withstand the next attack, or will it be the next headline?
At Relevant Software, we don’t just find security flaws—we eliminate them. Our expertise in:
- AI-driven security testing
- Penetration assessments
- Compliance-driven mobile security
- Quality assurance services
…ensures that fintech, healthcare, and enterprise applications remain resilient against modern threats.
Don’t wait until an attack exposes your mobile app. Secure it today with expert testing solutions from Relevant Software. Contact us!


Hand-selected developers to fit your needs at scale! Let’s build a first-class custom product together.

