Solve the Lack of Resource by Outsourcing Cybersecurity
As businesses’ appetites for technology expand, so does their exposure to cyber threats. But, as companies struggle to build their defenses, they find themselves locked in a battle for resources. The solution?
Well, 81% of corporate leaders are choosing to rely on third-party vendors to either completely handle or supplement their cybersecurity functions, according to the Deloitte Report 2022. This surge in outsourcing is a response to the cybersecurity industry’s equally rapid growth. Canalys’ latest cybersecurity forecasts report that global cybersecurity spending (encompassing enterprise products and services) will swell by 13.2% in 2023. This growth trajectory indicates a mammoth total spending of $223.8 billion in the best-case scenario, with cybersecurity services skyrocketing faster than product shipments.
200+ companies from 25 countries outsourced software development to Relevant
We provide companies with senior tech talent and product development expertise to build world-class software. Let's talk about how we can help you.
Contact usLet’s take a moment to decode this. Cybersecurity, though vital, can be a resource-intensive endeavor. It requires specialized skills, state-of-the-art technology, and an unwavering commitment to continuous monitoring and defense. With a global shortage of cybersecurity talent and the costs associated with building an in-house security fortress, businesses are finding cybersecurity outsourcing a panacea.
Table of Contents
Can Cybersecurity Be Outsourced?
If you’re contemplating the idea of drawing on external expertise for your company’s cyber defenses, let’s clear the air. As we mentioned, most businesses have already turned to IT security outsourcing for various aspects of their cybersecurity operations. This includes security monitoring, vulnerability management, physical security, and employee training.
These outsourcing cybersecurity statistics suggest that organizations increasingly recognize the benefits of outsourcing cybersecurity tasks. Although making this decision should be well-thought-out, it is certainly worth considering for its numerous advantages, including access to specialized skills, cost-effectiveness, and improved security measures.
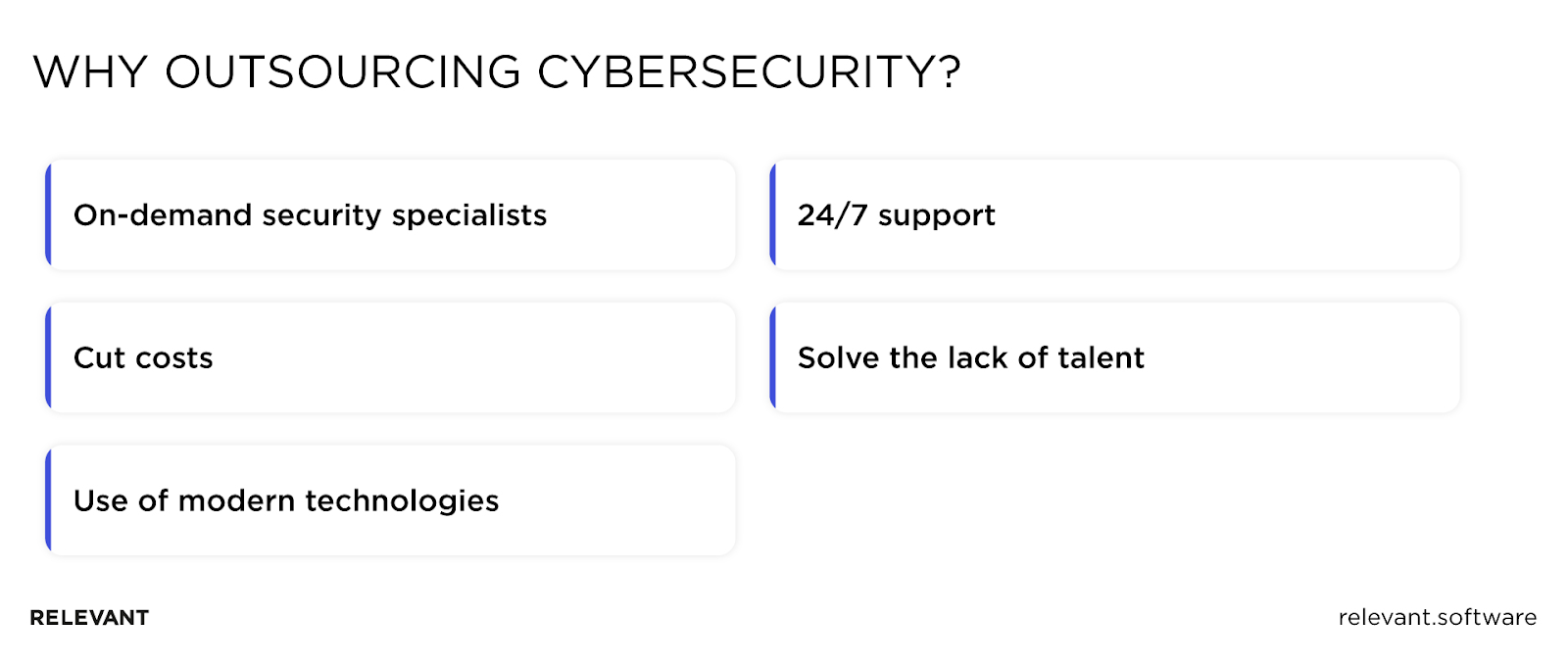
Why Outsourcing Cybersecurity?
In an age where digital threats continue to evolve and multiply, protecting your business from potential cyber-attacks is more critical than ever. So, let’s dive into the strategic advantages outsourced cybersecurity can bring your enterprise.
Lack of experts
While an in-house IT team offers many advantages, the escalating sophistication of cyber threats demands an even higher level of expertise that often surpasses the capabilities of these internal teams. Additionally, today’s business landscape faces a significant talent gap in the cybersecurity industry. This gap, coupled with the complexity of identifying and neutralizing threats, prompts many businesses to consider IT security outsourcing.
Engaging with external service providers alleviates the burden of managing complex cybersecurity tasks and opens avenues for in-house teams to enhance their skill sets. Cybersecurity specialists can help uncover vulnerabilities that may have been missed, thereby minimizing the risk of data breaches stemming from human error or weak spots.
Outsourcing cybersecurity is an efficient solution that offers businesses access to specialized knowledge and tools which may otherwise be out of reach. More importantly, it allows businesses to focus on their core operations, knowing that a team of professionals is safeguarding their digital landscape. Thus, outsourcing emerges as a strategic decision, contributing to peace of mind and improved security posture.
More cost-effective
Navigating the cyber threat landscape is a costly endeavor, particularly given the premium salaries of skilled cybersecurity professionals. Generally, the financial burden of maintaining an in-house security team can prove challenging. The expenses for having internal experts extend beyond wages to ongoing training and investment in cutting-edge technology. A cyber security breach definition refers to unauthorized access to sensitive data that can damage a company’s finances and reputation. The costs of responding to such breaches, ensuring staff readiness, and addressing cybersecurity issues can significantly impact your company’s financial resources over time.
Outsourcing security services while providing robust security protection also delivers cost-effectiveness, making it a preferred strategy for many businesses. Cybersecurity outsourcing companies offer flexible, affordable solutions suited to the needs of diverse businesses. You can access the skills and experience of dedicated cybersecurity experts who stay abreast of the latest cyber threats and countermeasures. Understanding which countries offer the best services can be beneficial, so you can check the top 4 countries to consider for outsourcing your software development and cybersecurity needs.
Stay up-to-date as technology evolves
Cyber threats evolve rapidly alongside technology, requiring specific skills and a deep understanding of the digital ecosystem. In-house IT teams, often overwhelmed with multiple tasks, might find it challenging to keep up with the latest security vulnerabilities, thus making a case for outsourced IT security.
Beyond providing dedicated professionals, outsourcing cybersecurity ensures these experts continually adapt to technology’s rapid evolution. Furthermore, their singular focus on cybersecurity enables them to provide businesses with the most up-to-date protection mechanisms and strategies. With sophisticated network setups, cybersecurity firms often use advanced solutions like AI and machine learning for efficient and faster vulnerability scanning and threat detection, outperforming manual inspections.
By leveraging outsourced IT security, you gain the advantage of an agile team that evolves with technology and identifies vulnerabilities with heightened accuracy. This team ensures robust protection against evolving cyber threats, a crucial factor, especially as web application security vulnerabilities become more prevalent in a digital business landscape.
Ensure your business stays compliant
Compliance can be a significant challenge for businesses, particularly when data breaches and cyber threats are on the rise. Stringent regulations such as the GDPR impose heavy penalties on non-compliance. These fines can reach up to €20 million or 4% of the company’s total global turnover.
Every business, regardless of its size and niche, is a potential target for cybercriminals. The assumption that smaller companies might be immune due to their size is a misconception that can lead to severe repercussions. The implications of a data breach are far-reaching, surpassing financial loss to include reputational damage and declined customer trust, factors that can gravely affect a business’s long-term viability. Therefore, it is critical for companies, regardless of their size, to ensure comprehensive data protection.
By leveraging cybersecurity outsourcing, you will benefit from a proactive approach to compliance, given the increase in international data collection and the associated risks. Through IT security outsourcing, companies can ensure they are prepared for these developments and make a strategic move to safeguard their digital assets while ensuring compliance.
Dedicated security specialists on-hand
The world of cybersecurity is dynamic and multifaceted, presenting challenges that require specific expertise and constant vigilance. For many businesses, particularly smaller ones, having an in-house IT staff with such specialized knowledge can be an uphill battle. In such a scenario, the decision to outsource cybersecurity becomes a strategic game-changer. Through hiring cybersecurity experts, businesses gain a dedicated team that monitors the evolving tactics of cybercriminals, identifies network vulnerabilities, and implements robust defenses.
When dealing with cybersecurity threats, swift and decisive action is as critical as prevention and detection. By outsourcing cybersecurity services, businesses invest in a quick-response team that rectifies issues promptly, thus minimizing potential damage and preserving the company’s reputation. Such a strategic blend of expertise, vigilance, and timely action forms a reliable shield against the ever-evolving world of cyber threats.
Round-the-clock protection
Maintaining constant vigilance 24/7 is crucial but can be challenging for an in-house IT team that operates within conventional business hours. Outsourcing IT security solves this challenge by providing companies with round-the-clock protection against potential cyber threats.
Cybersecurity service providers use advanced monitoring tools and AI-driven threat detection systems, ensuring continuous surveillance of your networks and systems. Whether a threat emerges in the middle of the day or the depths of night, these professionals are ready to spring into action, preventing or mitigating damages and ensuring your business operations remain secure and unaffected. With outsourced IT security, you ensure that expert protection is always on guard, giving you peace of mind.
Most popular cybersecurity functions outsourced
Not all functions require an on-site presence, which is why many businesses find value in outsourcing certain cybersecurity tasks. So, let’s understand the most common choices for outsourcing.
Security operations
Security operations, often called a Security Operations Center (SOC), are among the most widely outsourced functions. The SOC is a hub of consistent surveillance, assessment, and defense against potential cyber threats, aimed at bolstering the security of an organization’s IT infrastructure.
Having a managed SOC goes beyond merely deploying high-tech security systems; it calls for assembling a specialized team of experts. This includes security analysts who scrutinize potential weaknesses, forensic investigators who conduct comprehensive analysis following any detected breach, and incident responders for swift threat mitigation. By outsourcing IT security operations, companies have a team working around the clock, ensuring that no suspicious activity goes unnoticed, thereby providing relentless protection for their digital assets.
Vulnerability management
This crucial operation involves systematically identifying, evaluating, and rectifying weaknesses in an organization’s IT infrastructure, including networks, applications, and systems. By entrusting this task to specialized external providers, companies gain access to expert insights, state-of-the-art tools, and methodologies that keep them ahead of potential cyber threats. Consequently, organizations can bolster their cyber defenses and mitigate risks through outsourcing vulnerability management.
Employee education and training
Since human error often serves as a weak link in cybersecurity, equipping employees with the knowledge and skills to identify and counteract threats is paramount. Employee education stands out for its high impact on organizational safety. By outsourcing this function, organizations can leverage expert-designed curriculums, up-to-date content, and engaging training methodologies. This approach fosters a culture of security awareness that permeates throughout the organization.
Cybersecurity Outsourcing Risks
By entrusting vital security functions to an external organization, companies try to find a delicate balance between gaining specialized expertise and maintaining control over their data and systems. Let’s review some potential challenges and outsourcing security risks to help you make informed decisions about adopting this strategy for your organization.
Partial control
When you engage external companies or freelancers, there’s an inherent risk of losing control of how cybersecurity tasks are performed and monitored. But that shouldn’t be a significant concern as long as you know and trust who you’ve hired. That’s why a careful selection of a trustworthy provider will help you mitigate these concerns and avoid IT outsourcing failures.
Hidden costs
Cybersecurity outsourcing, while beneficial in many respects, can sometimes involve hidden costs that could offset the expected savings. These might include the costs for knowledge transfer, system integration, or unexpected operational expenses, which aren’t always factored into the initial estimate. Also, businesses might encounter additional charges for services beyond the contract’s scope. Therefore, ensuring that your service agreement is comprehensive and clear on potential additional expenses is crucial to avoid unexpected costs down the line.
Data sensitivity
In today’s data-centric world, upholding strict data protection standards is crucial, especially when outsourcing processes involving sensitive customer information. By sharing this data with external entities, you might inadvertently expose your business and customers to potential security risks as control over data shifts to the outsourced party. Therefore, it’s essential to thoroughly vet any third-party providers and ensure they adhere to the highest standards of data privacy and security.
Reliability and quality concerns
It’s possible that the standards and efficacy of an external provider may not align perfectly with your business requirements or expectations. Further, response times during critical security incidents may vary, potentially leading to increased vulnerability. Therefore, it’s essential to thoroughly assess potential service providers, scrutinize their service level agreements, and ensure that their quality and reliability metrics align with your organization’s needs before proceeding with cybersecurity outsourcing.
What Functions Can Be Easily Outsourced Offshore
Typically, process-driven tasks that require specialized knowledge or consume significant internal resources are prime candidates for offshore outsourcing. Here, we explore some of these functions that can be outsourced offshore smoothly, providing value and efficiency to your operations.
Service desk capabilities
This critical feature ensures seamless, 24/7 service delivery, enhancing your business operations’ reliability. The service desk continuously monitors services and is integral to the day-to-day management of core activities. With its strategic implementation, an outsourced service desk can catalyze efficiency across the organization, fostering a superior user experience while enabling your internal team to focus on core business competencies.
Data center outsourcing
This strategic move involves delegating the daily operational responsibilities associated with servers or host platforms, including distributed servers and storage systems. This goes beyond mere hardware management and involves the systematic oversight of computing and storage resources.
Network services
This facilitates network operation. Leveraging protocols at the application layer of the Open Systems Interconnection (OSI) model, it offers server services that are designed to operate across multiple servers. It equips a company’s network with the capabilities to perform basic functions like NTP, DNS, DHCP, VoIP, File and Directory, Hardware Sharing, Email, and Website Hosting.
Managed security operations
It refers to the comprehensive management of critical operational components such as policies, procedures, equipment, data, human resources, and external contacts. This holistic approach ensures the overall effectiveness and fortification of a business’s cybersecurity. It also encompasses the physical components and services that support vital business functions. Infrastructure management comprises all the elements and components that enable the execution and access of data management functions, along with other related services.
New application development
This function involves creating innovative software solutions that improve a company’s operational efficiency and foster growth. A team of professionals is typically entrusted with conceptualizing and developing applications tailored to meet the company’s unique requirements and aspirations.
Legacy system maintenance
Otherwise known as software maintenance, it focuses on enhancing the performance of existing software systems while minimizing the potential for errors or system failures. Legacy systems maintenance employs codes and AI for early warning detection.
Testing and QA services
These services play a critical role in validating the intended software’s functionality and performance. They encompass a wide range of testing procedures, including functional testing, usability testing, performance testing (it includes load and stress), security testing, compatibility testing, and mobile app testing.
Packaged software implementation and management
This function ensures that software packages are deployed and utilized to their maximum potential. By creating system and process changes, critical business decisions can be reviewed and finalized well before system configuration. It includes offerings that provide customers with ongoing support and maintenance for dominant packages.
How to choose a reliable cybersecurity partner
Choosing the right cybersecurity partner is a critical business decision requiring careful consideration and scrutiny. A reliable partner can mean the difference between maintaining a secure, robust digital environment and facing potentially catastrophic cyber threats. Let’s find out how to identify a partner that aligns with your needs and delivers the level of security your business requires.
You can also check our comprehensive guide on the software outsourcing vendor selection process and criteria for more insights on this topic.
Experience
The best cybersecurity and risk management firms can demonstrate their work in the IT field. They have years of experience on top of a portfolio of services that match their clients’ needs. They will demonstrate willingness and capacity to get the job done. They can provide case studies as evidence of customer success and clearly articulate exactly how they help their clients, backed by measurable results.
Skill set
Security companies may have vendor-specific certifications and training from accredited institutions. Top-rated security professionals will openly display their awards, recognition, and certificates. Ask to see them if they are not displayed on their website. Inquire about specific staff certifications and training. You want to evaluate the team, not just the company.
Customer satisfaction
The company should be able to provide examples or stories of how they solved a customer’s issue or managed a customer’s project and how they successfully solved a problem. It is also essential to get in touch with past and present clients for more evaluation and due diligence.
Reporting practices
When outsourcing any service, especially one as complex as cybersecurity, your company will need visibility into what is being managed and the results. Leading cybersecurity firms and managed security service providers will have established monthly analytic and reporting expectations to ensure transparency with their business customers. To further protect against any breaches in your network, in-house IT specialists should be in contact with them.
Forward-thinking
Cybercriminals are dynamic and always finding newer ways to breach systems. The best cybersecurity firms will be knowledgeable of past, current, and potential future threats as well as the technological solutions needed to combat such threats. To be effective, leading security experts must stay up-to-date on the latest trends and techniques attackers use.
Reputation and reference
Ask for active client references and reviews to gauge performance, responsiveness, reliability, and expertise. Customer feedback can shed light on the operations of a potential outsourcing firm and whether it aligns with your organization’s needs. Customer feedback should also clarify where the firm is lagging behind.
Partner with Relevant Software for Cybersecurity Outsourcing
Cybersecurity is not an area where any business can afford to take risks. Outsourcing your security needs to a trusted partner like Relevant Software allows you to concentrate on your core business without worrying about potential cyber threats. With a proven track record and a robust, comprehensive suite of cybersecurity services, we are committed to safeguarding your business against the increasingly complex landscape of cyber threats. You can easily outsource cybersecurity functions to us:
- Vulnerability assessment to perform tests and identify security breaches and vulnerabilities.
- Mobile and web security to protect your applications from penetration.
- Cloud security to prevent data leaks in cloud platforms due to common flaws and mistakes.
- Application security to prevent app intrusion and compromise.
- Overall security testing to ensure you are properly secured.
As an established IT outsourcing services company, we at Relevant prioritize your business’s security as our primary concern. Our goal is to provide a secure digital space that allows your business to prosper and grow. Trust Relevant Software to be your steadfast cybersecurity partner, shielding your organization from risks while you focus on leading your business toward success.
FAQ
Our core services:
Do you want a price estimate for your project?
Do you know that we helped 200+ companies build web/mobile apps and scale dev teams?
Let's talk about your engineering needs.
Write to us